Dear Tobias, how would you describe CyberTrap in 3 quick-witted words?
Last Line of Defense!
Please introduce yourself briefly and tell us something about your background.
After studying computer science, I spent almost 20 years at Sun Microsystems working on the internals of the Unix operating system Solaris. Through in-depth analysis of problems in the operating system and network and the search for bugs in Solaris, I was able to expand my knowledge of operating systems. This knowledge brought me to CyberTrap, where we monitor attackers and tools at the operating system level to reveal attack techniques and attackers’ intentions. I have been working at CyberTrap for three years as a Solution Architect and Sales Engineer.
What makes CyberTrap stand out?
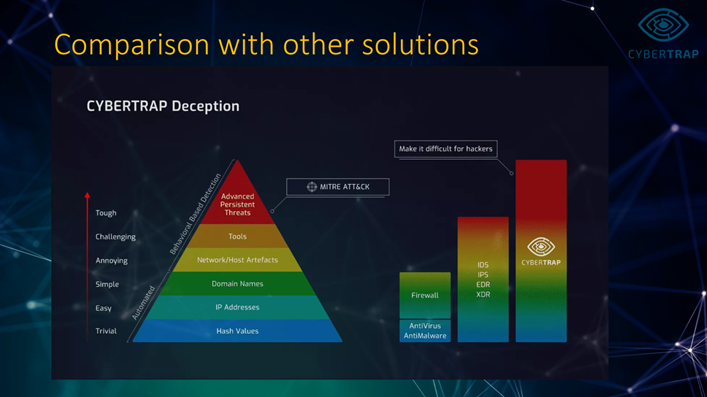
The CyberTrap adds another pillar to security. Deception strategies are known from many areas: they can even be found in nature, and warfare is unfortunately probably the largest area of application. MITRE is also a great advocate of deception in IT and urges that this tactic should not be left unused. I think the term “hacker engagement” [MITRE] is very apt. We are reversing exactly what the “Prevention” pillar does: CyberTrap subliminally offers the attacker systems that he can scout out and use. They appear to be the central file share server, a database management system or an SAP instance. These are also real systems, but they have no use in production. Instead, they have a monitoring component that observes and exposes the attacker and his tools.
Our deception technology originates from a real use case of SEC Consult, who used honeypots in a breach analysis and then pursued consistent further development in order to have more than just additional alarms. When the product was ready for the market, CyberTrap Software GmbH was founded as a spin-off.

How does CyberTrap help companies?
The use of our deception technology provides additional security. First, we improve intrusion and threat detection with real alarms at an early stage of the attack (reconnaissance). With our trap systems, we extend the company’s attack surface to include systems that have no relevance to production and are not required or used by normal users. So if there is activity on our systems, this results in real alarms that need to be prioritized.
By raising alarms in the early attack phase, we shorten the dwell time, i.e. the time until we as defenders become aware that we have an attacker in our network. So we gain time.
We also prevent damage to the production systems when the attacker is wreaking havoc on our trap systems. We can observe him and understand what his intentions are in the attack. Generally speaking, this is how we create threat intelligence.
It now depends on the company’s defense strategy whether it should react immediately to the CyberTrap alerts via SIEM, SOAR and XDR on the IOCs automatically and thus use the improved detection, or whether it should also determine the attacker’s approach and intentions in order to better protect itself against them.
What do you perhaps see slightly differently from prevailing opinions in the field of cyber security?
There is an opinion here and there that hacker engagement based on deception only makes sense once a certain level of maturity has been reached. I don’t see it that way at all. On the one hand, basic security measures are often already delivered as on-board resources. Secondly, Hacker Engagement does not require any other components to be installed. It adds another pillar to the traditional ones in security: traditionally, we have Prevent, Detect and Respond. With Engage as a method and Deception as the underlying strategy, we are introducing a completely new additional technology. And nobody should miss out on the advantage of real alarms – even at an early stage of an attack.
Should a customer have a certain level of cybersecurity maturity to be able to use deception technologies successfully?
As already mentioned in connection with the previous question: no. If the customer has already outsourced (security) services, they can also use a managed service from CyberTrap: from installation, configuration to operation and, above all, analysis in the event of an alarm, they can also use Deception as a cloud-based service. And he could even add Deception at short notice in the event of a specific intrusion – experience shows that damage is often already present in the form of compromised systems or encrypted data and all concentration is put on restoration or even reinstallation.
What’s next – what’s on your technical roadmap, what are your plans?
First of all, we are focusing on the further development of our core product, CyberTrap Deception Technology: we will use “cases” to automate the analysis of alarms and events, thereby reducing the workload for security engineers. We will also offer “stories” to speed up the configuration of the environment. These are ready-made deception environments for specific purposes. AI-generated fake data is stored on the decoys, which is customer-specific and keeps the hacker busy.
We will also make threat intelligence that partner companies generate with our technology available to our customers via their CyberTrap dashboard.
If you could send an email to all CISOs to address a security issue, what would you choose?
Use deception strategies in your IT security to defend yourself that have long been used successfully in martial defense. Add another pillar to your security with this hacker engagement!






