Compare Security Operations Center (SOC)
Looking For A
Managed Security Operations Center or Managed Detection & Response?
Cybersecurity Basics
What Is a SOC?
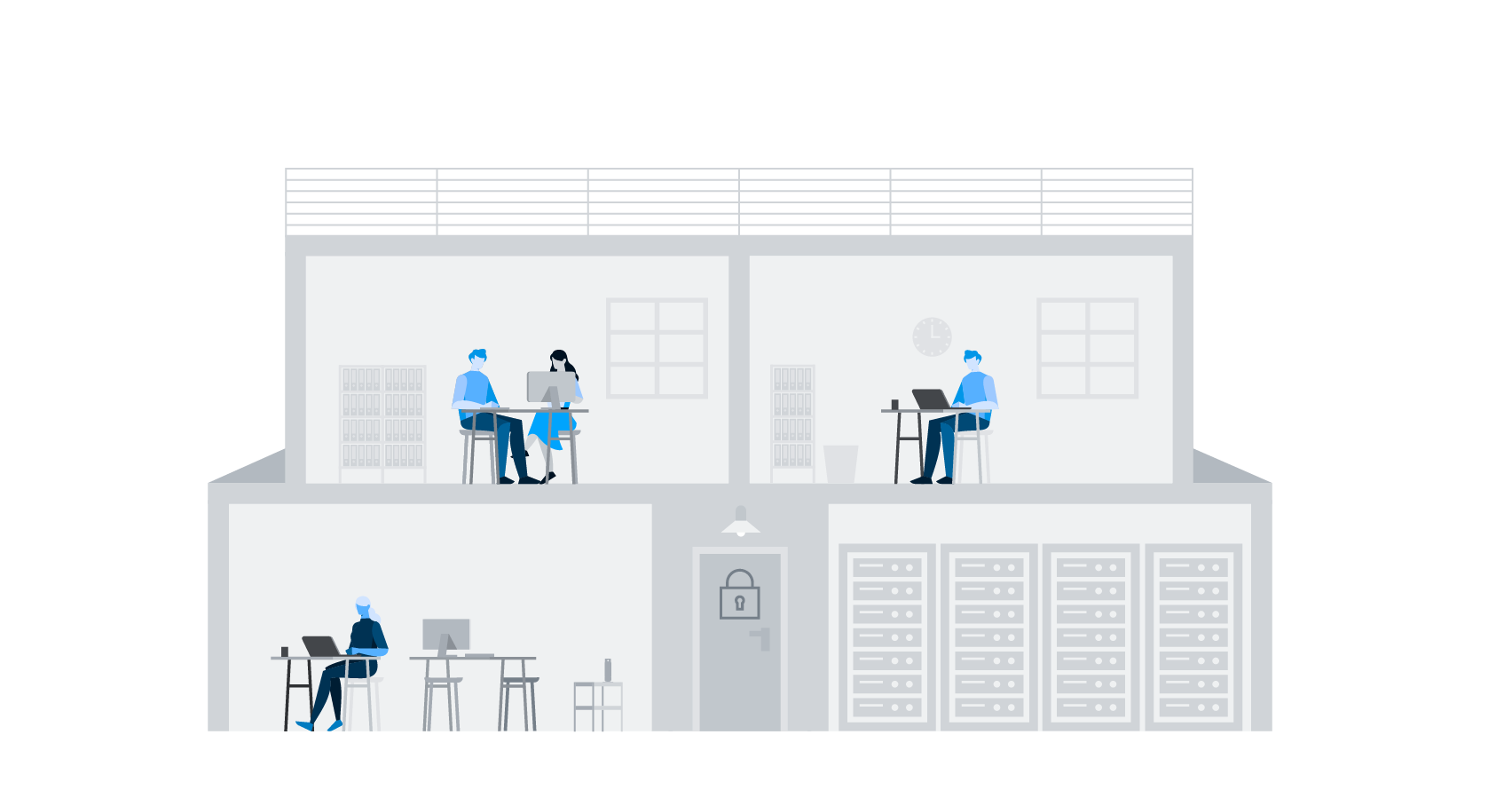
Security Operations Center (SOC) is a specialized unit within an organization that continuously performs security monitoring, analyzes security incidents and responds to them in order to protect the IT infrastructure from cyber threats.
Three Main Areas
How A Security Operations Center Works
A SOC can be divided into three main areas:
Protect
Typically, a SOC tracks various security alerts, including messages from tools about potential threats as well as information from employees, partners and external sources. Many modern SOCs use a SIEM system to centrally collect and manage alerts.
Detect
The reported threats or incidents are investigated by the experts in the SOC to ensure that they are not false reports that turn out to be harmless.
Respond
If a security incident is confirmed and a response is required, the case is forwarded by the SOC to the appropriate individuals or teams to take countermeasures. With a playbook agreed with the customer, the SOC/MDR partner also reacts directly in the customer’s infrastructure to contain an attack, e.g. by isolating endpoints.
Compare SOC Provider With Us
You Can Receive Offers From the Following Providers - And All Others
At CyberCompare, we help you find the right Security Operations Center for your company in a resource-efficient way, so you can ensure the security and availability of your systems and data. With us, the large field of cybersecurity becomes manageable for you. You can get an initial overview of possible SOCs in our provider directory.
Simple. Clear. Affordable.
How A Typical SOC Project With Us Looks Like
Target Definition Of The Future Concept
Target definition and development of the future concept in several workshops. This includes the target architecture (e.g. SIEM- vs. XDR-based) and the question of what is provided internally or outsourced (e.g. co-management of the SIEM solution or SOC analysis).
Result: Defined procedure/objective for the tendering of the target scenario
Tender Preparation & Specifications
Workshops to record the requirements (scoping) and iterative adaptation of the specifications after consultation and clarification of open questions
Result:
- Specification of an anonymized specification sheet for the tender/comparison of offers
- Selection of a longlist of 5 providers for the invitation to tender
Offer Comparison & Decision Preparation
Request for tenders from defined providers – can be anonymized
Coordination, consolidation and preparation of the offers as well as evaluation with a recommendation regarding top providers and concepts in comparison with the specification and the target concept
Creation of a report with a clear award recommendation & visibility of the differentiating features
Result: Basis for a qualitative decision for 1-2 providers for final negotiation and awarding of contract
Optional
Support With Commercial And Legal Contract Negotiations
Result: Signed contract with 1 provider
Optional
Support With Onboarding The Solution
Result: Productive SOC service as part of the coordinated onboarding plan
Optional
360° Inventory And Market Study
Part 1: Inventory & diagnostics of IT & OT security
Part 2: Overview of the market and derivation of a strategy
Result: Decision on a suitable solution and procedure for SOC selection
valuable insights from our expert
What Differs SOC Providers? Find Out In Our Interview
Maximum defense with the right knowledge
What Is A Good Security Operations Center?
Modularity
A good SOC service provider offers a modular offering that enables customers to start with a reduced scope and then develop further as required.
Transparency
Price structures should be clear and understandable, with no hidden costs. Volume-based license models can be difficult to calculate. A good service provider offers alternative licensing options that are tailored to the customer’s individual requirements.
Clear Core Competence
As security is a multi-faceted field, you need to be confident that your service provider has the expertise to protect you. It’s important to make sure that the SOC service provider you choose specializes in security and doesn’t just offer it as an add-on service.
WHITEPAPER
The Successful Selection of a Partner For Your Managed SOC
A Security Operations Center (SOC) has the task of permanently monitoring a defined IT environment for security-relevant events. This usually involves analysing log files and/or data traffic for suspicious information. The aim is to detect threat scenarios and initiate appropriate countermeasures (“response”).
In this whitepaper, we address the key issues in the specification of requirements, as well as success criteria in the selection process.