Hello everyone,
relationships only harm those who don’t have any. That’s what the former Chancellor of Austria probably said to himself and founded a cybersecurity startup with a billion-dollar valuation, a noble claim (protect nations) and a wide-legged appearance (Dream Security) => I’m curious to see what else we’ll hear from here. The mentioned turnover of ~130 million/a after 2 years is really strong, hats off!
The OT experts among us have probably already taken note of the newly published Gartner Magic Quadrant on OT NIDS (Cyber Physical Systems Protection Platforms, CPS PP), which includes good aspects in the selection of solutions. Armis, Claroty, Dragos, Microsoft and Nozomi are listed as leaders – you can then request the report from them free of charge. However, some solutions that are widespread in this country, such as Rhebo, Asimily (see also below), Genoa, IRMA, Siemens or Omicron , are completely missing from the report.
Worst experience using a cybersecurity product? : r/cybersecurity => According to the anecdotes, there is no security solution in the world that has not earned at least 1 fanatical full-time hater. CyberArk, Symantec and Sophos are particularly popular in the thread, according to my small statistics. To smile in between (“wE hAvE a NeW fEaTuRe On ThE rOaDmAp!” Oh f*** off James from sales, that feature is 5 years behind your competitors. We already pay for your product, why are we talking?! Let me talk to a tech who can tell me why the agent is running hotter than chrome with 100 tabs open. Y’know the ONLY reason why I agreed to this call.”). With a sufficiently large customer base, you can of course always find someone who is completely annoyed.
Hardware-enabled security as an additional layer of protection: Both Intel (vPro) and Nvidia (Bluefield, Morpheus) offer functions for monitoring host integrity or, for example, secure remote access even if the operating system is compromised. And at Nvidia, of course, the acceleration of AI-supported anomaly detection. Some of the functions also help EDR and NDR systems – MITRE has already provided mapping to the ATT&CK technologies for the Intel platform, Microsoft Defender and Crowdstrike are explicitly listed, Nvidia Morpheus can be used with Crowdstrike, Armis and Check Point , among others.
A few observations on tenders for managed security services:
- Offers with service delivery from EU nearshore countries (e.g. Bulgaria, Romania, Poland) are typically ~50% lower than offers for service provision by employees in Germany, Austria or Switzerland (prerequisite for this is that contractual partners in both cases are well-known MSSPs, i.e. not local garage companies)
- The technical qualification of the security experts is usually comparable, in any case not systematically worse (of course, you can be unlucky in both cases)
- What sometimes makes the difference is actually the German language skills. And that’s not because of the customer contacts in IT – they usually speak good English. Instead, we often have a lack of language skills or a lack of willingness to deal with the problem with the computer with someone in English
- If that were not the case, we would probably sooner or later have conditions like in the UK, despite the GDPR. There, IT and IT security operations are already largely in the hands of Indian giants such as Tata, Infosys or Wipro, which boast daily rates of ~300 EUR and an enormous number of reference customers
- On the one hand, this is positive, as we are preserving well-qualified and well-paid jobs in the state. On the other hand, of course, it’s bad, because we pay significantly more for our IT operations than would still be necessary from a technical point of view
- It will be exciting to see how this develops. Wage levels will converge, but we are already seeing good German-speaking security specialists from Eastern Europe in some tenders for managed SOCs, etc. And AI is certainly not getting worse in terms of near-real-time translation capabilities and other productivity gains.
- It is also interesting that Kyndryl or Eviden , for example, succeed in using nearshoring to convert former loss-making service contracts into those with lucrative margins – while at the same time offering more favorable conditions for customers. Both companies are suffering from the past: IBM used to sell Kyndryl Services as a “loss leader” in order to place the products with customers. The predecessor organization of Eviden had a similar experience with Atos.
- In a podcast, I heard that waterworks in North Rhine-Westphalia now offer a sector-specific managed SOC and thus compete with established providers. Small rule of three:
- Approximately 30,000 companies and public bodies in Germany are affected by NIS-2. We can assume that this is the absolute upper limit for the number of potential SOC customers
- At the same time, there are about 150 providers of MDR and MSOC services active in this country (in my opinion, MDR and MSOC both serve the same 24/7 surveillance market, i.e. those who have the MDR service at Arctic Wolf, SentinelOne or Crowdstrike, for example, will not additionally book a SOC)
- Each of these providers already has an average of 100 customers (the big ones more, the small ones less). This means that half of the theoretically possible customers (150×100=15,000) are already existing customers of some SOC or MDR provider.
- However, weighted by the number of endpoints/users/log volumes, the companies and public clients that already have an MDR/SOC today certainly cover 80-90% of the market potential.
- Of course, there are still opportunities for growth in that additional log sources/sensors can be connected and additional services such as vulnerability management or incident response can be sold
- Conclusion: Managed SOC is already essentially a cut-throat competition. You can also see this in our tenders. In very few cases, these are customers who have not yet had continuous monitoring at all – normally it is a matter of a new assignment, and it is not unusual for the customer to receive better conditions than 3-4 years ago. Customers with fewer than 1000 endpoints typically opt for a standardized + affordable MDR service.
Other perspectives / figures? Always happy to let us know.
Noteworthy M&A:
- Microsoft buys a stake in VEEAM from Insight Partners and thus enters the backup and recovery business. If only perimeter firewalls are missing, then E2E Security is available from a single source. VEEAM was probably valued at ~15 billion USD – with 550,000 customers worldwide, this sounds halfway understandable when compared to Rubrik (~7 billion) or Cohesity (~4 billion)
- CyberArk Acquires Zilla (Identity + Access Governance Automation)
- Nozomi übernimmt XONA (OT Remote Access)
Notes from vendor conversations:
Trask:
- Czech IT/Security Service Provider, approx. 1000 employees
- Kunden u.a. Siemens, Deutsche Telekom, ING, Société Générale, BNP Paribas, Generali, Visa
- Managed SOC, Zero Trust, Pen Tests, GRC Consulting, many reference projects for Identity Governance / Access Management
- Sales / Customer Manager in DACH, Delivery from EEU => Of course, some of the prices are very attractive (e.g. 7 person-days pen test of medium complexity for ~5 thousand EUR mentioned)
Asimily (Update):
- OT-/IoT/IoMT-NIDS for inventory, vulnerability and attack detection (similar to Medigate/Claroty, Nozomi, Dragos, Armis…) from the USA, approx. 100 employees
- About 250 customers, in EU e.g. University Hospital Tübingen, Ulm, Heidelberg, Freiburg, Hanau
- So far, a clear focus on healthcare / medical technology (probably already > 1 million X-ray machines, patient monitors, etc. in monitoring), but also many industrial applications
- Passive approach, optional active polling with OEM commands
- Architecture as usual: sensors via mirror ports, central engine either on prem or as SaaS
- Deep Packet Inspection for ~200 logs
- With your own recommendations for action for medical technology devices based on empirical values for the implementation effort, also integration with emtec Catalog => Real added value
- Exciting feature: Automated SW distribution (patch management) for the accessible devices. The OT NIDS top dogs still have to step up their game.
- Also exemplary: A publicly available, independent laboratory test by the US Department of Energy, in which the accuracy of asset detection and interference-free use during active scanning was tested. Some devices (7 out of 33) that were connected via serial interfaces or that did not send traffic through the measurement point were not detected. Interestingly, active scanning hardly detected any more devices, but provided significantly more open ports and device information. And caused a malfunction in an SMA inverter. Unfortunately, there is only a comparable test report for RunZero so far.
- There are probably still weaknesses in the correct assignment of device types based on network data, in some cases individual devices are identified multiple times as different assets
- Licensing based on reachable ports
- Channel partners in the DACH region: A1, Axians, Cancom, others are of course to follow
Avepoint:
- Solution and service provider from the USA specializing in M365 data security, ~2500 employees, used by many large companies
- I.e., complementary solutions such as long-term and granular backups + restoration of Sharepoint, Dynamics, Azure, Power Platform (licensing usually based on number of users). Similar solutions are also offered by VEEAM, Commvault, Cohesity, Rubrik, Skykick, Retrospect or Hornet, for example
- Interesting: Storage space optimization of M365 data (“Opus”) via rule-based archiving. As a first step, a free potential analysis is carried out => Feel free to take a look if the Microsoft storage costs explode
- Everything in Azure data centers, i.e., probably not 100% perfect from a redundancy point of view
- In addition, migration services (on prem => cloud) and offers for operation including governance/policies
- Customers in the DACH region include VW, Nestlé, Siemens Healthineers
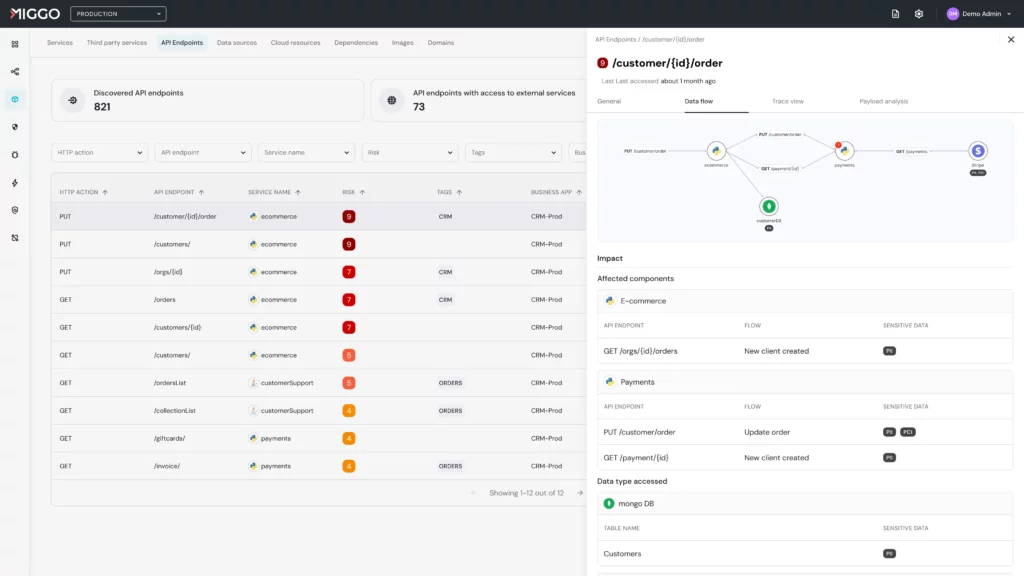
Miggo:
- Israelisches Startup für Application Detection & Response
- ~10 enterprise customers in the USA and Canada, focus on customer facing web applications (e.g. Elastic, ZScaler, Best Buy)
- Concept: Virtual patching in the application as a supplement to “normal” patch management to deal with the problem that the number of known open vulnerabilities in most infrastructures is constantly greater than zero, and often even grows steadily.
- In addition, more precise detection of attacks against EDR
- Observes logs and telemetry, also using its own sensor for cloud environments (“Runtime Communication Flows”)
- Helpful in risk management is the visualization of data streams between applications (as far as I understood, this is also a significant difference to Contrast) => see also screenshot in the attachment. This can then be used to analyze + prioritize the possible attack paths.
- We also offer a free assessment, so maybe take a look and try it out
As always: Questions, suggestions, comments, experience reports and also opposing opinions or corrections are welcome by email. Ditto for unsubscribing from the mailing list.
For the people who have received this email: Here you can register if you are interested or thaw the archive.
Regards
Jannis Stemmann






