Hello everyone,
Microsoft is slowly but steadily pumping the air out of the room where all the other security vendors are sitting. A few days ago, we looked at the new Microsoft Exposure Management solution together with a customer – another category that is offered to customers as part of a package, and which in many cases is good enough.
This is certainly one of the drivers of the consolidation that has been seen in recent weeks, particularly in the SIEM/XDR market: Cisco buys Splunk, private equity Thoma Bravo (also owner of Sophos, among others) buys Exabeam in addition to the existing portfolio company Logrhythm and wants to merge the two companies.
And then the next headline is that Palo Alto from IBM is taking over QRadar (the cloud variant – on premise customers are to be motivated to switch in the medium term) and the partnership between the two providers is being strengthened even further.
Could this be the next merger? A seamless integration of IBM Security and Palo Alto Networks would indeed be an extremely powerful platform.
In contrast to all other “suites” such as Trend Micro, Crowdstrike or Fortinet, the two companies would cover almost all security categories, including backup and recovery systems.
CyberArk also acquired Venafi from Thoma Bravo, for example. Venafi offers solutions for “machine identity”, i.e. in particular TLS and SSH certificate management.
How dangerous are cyber attacks really for companies?
Security solutions and services are sold primarily on the fear of cyber attacks. Some of us earn our living with security (me, for example).
Of course, we live in a bubble in which we always tell each other, into every microphone, how important further investments in security are. And in the headlines, multi-million sums always read very spectacularly.
But are the figures really frightening if you put the whole thing into perspective in terms of turnover, profit and other corporate risks?
From conversations with cyber insurance carriers and data from the FAIR Institute, we know some of the actual amounts of damage caused by ransomware attacks: An extremely severe cyber incident, including business interruption, causes losses in the order of 5-10% of annual revenue.
Listed companies have to publish the impact. Below I have listed some known incidents in a table and set the respective losses as a percentage of turnover and profit from the previous year (i.e. the financial year before the cyber attack). Sources are annual reports and newspaper reports, exchange rates are roughly rounded.
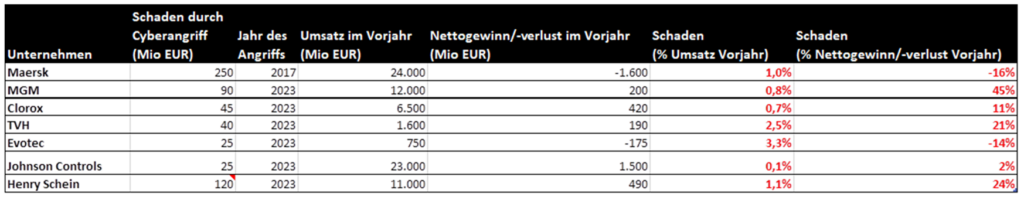
In my view, this leads to the following conclusions:
- Compared with normal fluctuations in business life, the impact of a cyber attack is usually negligible. Take MGM Resorts, for example: it sounds bad at first, damage amounting to EUR 90 million. But MGM made a profit of more than EUR 1 billion 2 years before that. And 3 years before that, it made a loss of EUR 1 billion (I guess due to corona). In other words, the cyberattack was almost irrelevant in terms of profits.
- Evotec and Maersk also made losses in the year before the respective attacks
- In relation to the turnover of a single year, the effects of the damage are in some cases only rounding errors. If you assume 5% of sales for the worst case, you are on the safe side.
- This is also in line with the typical recovery time objectives for operators of critical infrastructures (example: Colonial Pipeline, 6 days RTO => ~ 2% of annual turnover as damage due to business interruption)
- Conclusion 1: A healthy company (positive free cash flow, not overindebted) can easily cope financially with a successful cyber attack. Scaremongering is not called for here.
- Conclusion 2: This does not mean that investments in security are not worthwhile. On the contrary, the risks for employees and customers must of course be handled responsibly. However, the budget should be used in a targeted manner, and reasonable upper limits for ongoing expenditure can be derived from the figures.
If anyone has any counter-examples, of course! It is also clear that the effects on authorities, especially law enforcement or the defense sector, can be completely different.
Here are a few notes from provider briefings (not a provider recommendation, of course):
Cyberproof:
- Subsidiary of UST (larger IT company from the USA, approx. 24k employees). Cyberproof itself is the security division with approx. 800 employees worldwide
- Focus on Managed SOC / MDR and also provision of SOC analysts based on T&M
- Covered tech stack comparatively broad:
- SIEMs: Sentinel, Splunk, Chronicle, QRadar and occasionally also Elastic
- EDR/XDR: Crowdstrike, MS Defender, Cybereason
- Follow the Sun or for EU customers dedicated 24/7 from SOC in Barcelona (L1+L2) with L3 analysts in Israel/UK
- Reference customers DACH e.g. Dräger, Vaillant, Richemont, Nestlé, Schindler
- Target customers tend to be global companies with individual playbooks (including Axa and Maersk)
Island Security:
- Enterprise Browser – roughly somewhere between VDI and Web Proxy/CASB, I would say. As far as I know, CyberArk offers a similar product as part of its Identity Suite, as does Palo Alto.
- It works very well for restricting and monitoring/recording access to web apps and SaaS (incl. PAM functions). Particularly helpful for unmanaged devices => BYOD, external service providers and whenever proxies such as ZScaler, Netskope or similar are bypassed or do not work. Native integration with MS Conditional Access
- Blocking (“redacting”) of the clipboard/screenshots
- Can reduce the necessary scope of VDI (Citrix, VMWare, Microsoft)
- Based on Chromium
- Large financial groups (JP Morgan, but also SwissLife) as customers
- 5000 users => 120 EUR/user list price, resellers receive 40% discount
- Sequoia as VC investor, now valued at ~3 billion USD
Nasuni:
- Software for “NAS Unified” as a replacement for NAS and file servers, i.e., scalable enterprise file system especially for hybrid environments => fast local access times at low costs via object storage, good for cross-location collaboration
- With integrated backup + recovery functions (which is why we looked at this). Example: Immutable snapshots via own file system, which does not provide for manual deletion / modification of written files (not even with administration rights). However, according to my current understanding, attacks are still possible by setting up the retention time of snapshots.
- Not for databases, but for unstructured data (prime example: CAD files). Native integration with e.g. Siemens TeamCenter PLM or AutoCAD
- Customer brings their own object storage (public or private cloud) and their own encryption keys. The latter are not stored in the object storage, but on one of the decentralized access points (managed by the customer, no decryption options from the provider). Encryption is enforced (at rest and in transit).
- Already 1000 corporate customers worldwide, around 100 of them in the DACH region
- Exemplary: Transparent provision of e.g. current pen test and SOC2 Type 2 reports for download
- At a slightly higher level, I was impressed by the data sheet, which describes the advantages in a refreshingly clear and comprehensible way based on technical criteria. With security products, the marketing material usually impresses with cool pictures and creative word creations. It underscores the impression that the IT infrastructure/operations community is more mature and more mature in comparison.
We would also like to take this opportunity to thank you for your feedback and encouragement on our last market commentary!
- In fact, some of the security providers are loss-making according to GAAP or IFRS accounting (e.g. Rubrik: losses of around 50% of revenue in each of the last two financial years). In most cases, however, the companies are cash flow positive because we first transfer our SaaS license fees and then use them
- Are the high marketing + sales costs perhaps simply due to the fact that cybersecurity solutions are products that require so much explanation? => Also a factor, but in my view this is more due to strong competition, a lack of product differentiation and overinvestment by VC/PE companies. Other B2B categories that require explanation, such as automation technology, have much lower sales costs.
And here’s a treat for those of us who like to play / have played Civilization or other strategy games extensively (and perhaps also for anyone who is worried because their own children play so much computer games): Good gamers, good managers? A proof-of-concept study with Sid Meier’s Civilization (researchgate.net)
As always: Questions, suggestions, comments, experience reports and also opposing opinions or corrections are welcome by email.
Best regards
Jannis Stemmann
The Marktkommentar by Jannis Stemmann
Subscribe to Marktkommentar.
Gain More Insights Early On.
Marktkommentar includes insights from discussions with providers and customers on security projects and vendor briefings, questions and selective observations as well as unpopular theses in the security community.






