On June 24th, the draft of the NIS-2 directive was updated. Regarding the required measures for companies, nothing significant seems to have changed. However, the responsibility and liability of the management have been emphasized (§ 38): “Management boards of particularly important facilities and important facilities in accordance with § 30 are required to approve, implement, and monitor the implementation of the risk management measures in the field of cybersecurity to be taken by these facilities.”
In the reasoning for the law, I noticed upon re-reading:
“It is assumed that even with the complete implementation of the security standards prescribed by the NIS-2 directive, not all damage from cyber attacks can be averted.”
→ Undisputed, perfect security does not exist.
“However, if it is assumed that the implementation of the present guidelines can avert half of the annual damage caused in companies required to implement the NIS-2 directive, this results in averted damage of around 250,000 euros per company. Projected onto the estimated number of affected companies, this means averted total damage of approximately 3.6 billion euros (= 250,000 euros * 14,500 companies) for the German economy.”
→ Is this realistic? We are talking about important companies → And they are not starting from scratch with security but have already implemented many of the NIS-2 requirements. Advanced measures like phishing-resistant authentication, XDR/SIEM, NDR, or DLP are not required by NIS-2. A direct quote from a CISO of a corporation: “We still need to do a web training for executives, otherwise nothing really.”
→ But now comes the kicker: The additional expenses for the economy, especially for “bureaucratic costs from information obligations”, are estimated at 2.2 billion euros/year. Additionally, there are cost increases at the federal and administrative levels of 300-400 million euros/year. In the end, even with the aforementioned aggressive assumption, there is hardly any economic benefit left. Hopefully, the expanded reporting obligations will help us.
Here is the list of required measures so far (I have not found more concrete formulations in the 200 pages – if anyone has something substantial, always welcome): “Measures according to paragraph 1 shall comply with the state of the art, take into account relevant European and international standards, and must be based on a cross-hazard approach. The measures must at least include:
- Concepts regarding risk analysis and IT security
- Management of security incidents
- Maintenance of operations, such as backup management and disaster recovery, and crisis management
- Supply chain security including security-related aspects of the relationships between the individual facilities and their immediate providers or service providers (…may also include conducting External Attack Surface (EAS) scans…)
- Security measures in the acquisition, development, and maintenance of IT systems, components, and processes, including management and disclosure of vulnerabilities
- Concepts and procedures for assessing the effectiveness of risk management measures in IT security
- Basic procedures in cyber hygiene and IT security training (…This includes, for example, patch management, rules for secure passwords, restriction of administrative access accounts, network segmentation, and backup and security concepts for data… Regular training within the meaning of this regulation is offered at least every 3 years…).
- Concepts and procedures for the use of cryptography and encryption
- Personnel security, access control concepts, and asset management
- Use of multi-factor authentication or continuous authentication solutions, secure voice, video, and text communication, as well as secure emergency communication systems if applicable”
Good: The proportionality of the measures is also to be considered in terms of implementation costs (e.g., §30). Let’s see how this is practiced by the auditors.
Sophos conducted a cool survey – according to which 94% of all companies in Germany with more than 100 employees are already insured against cyber risks (85% in Austria and Switzerland respectively). According to my understanding, only classic policies were considered, i.e., no “Breach Warranties” as part of MDR services. This probably means we are already in pure competition in the cyber insurance market – I would have intuitively assessed it quite differently. On a global average (unfortunately, there are no country-specific results), the insurance covered ~63% of the damage in case of an attack.
However, despite extensive questionnaires and about 10 years of damage history, insurers still do not seem to be very good at selecting risks: The rate of ransomware attacks with successful encryption is lower in companies without cyber insurance than in those with cyber insurance. There is no significant difference in the rate of attacks without successful encryption. It certainly plays a role that attackers can assume that ransom will be paid by companies with cyber insurance (and corresponding coverage) and then proceed with more motivation after the initial access? Probably, the premiums for cyber policies are now so high that it is still worth it for insurers on average. And maybe the numbers are not that reliable – it is not clear whether the surveyed companies only took out insurance after the successful attack or already before. Maybe we can recognize trends over time.
Here are some notes from provider talks:
AttackIQ Flex:
- We already know AttackIQ from the Breach & Attack Simulation or Continuous Security Validation area (competitors e.g., Picus, Safebreach, Horizon3, Pentera, XM Cyber)
- Personally one of my “favorite categories” of tools because you can test many other security measures for effectiveness with them.
- Ideal also to prove to management “Yes, we tested MoveIT2 / Log4J etc. and are safe” when there is another attacker campaign or glaring vulnerability in the news
- The solutions are generally quite expensive and require high operational effort on the customer side. Therefore, in our experience, it is more suitable for large organizations with, e.g., their own Security Operations Team, possibly their own Detection Engineering, who frequently conduct Red Teamings and can then perform them more efficiently, and for example also automate rule creation for EDR/SIEM
- “Flex” is a new product variant – customers can download a pre-configured Pen Test script, which then conducts certain campaigns
- Afterward, the test results can be uploaded to AttackIQ and then interpreted together with an analyst from the provider. Reporting is of course standardized.
- Also interesting that only each individual test needs to be paid for, no ongoing license fees
- In my view, this increases the competitive pressure in the general pentest segment further. Because the solution (and others) are of course not only used by customers themselves but also by MSSPs and consultancies, who use it as an entry point for larger projects.
- What is hardly offered in an automated way so far are tests with specific goals like data theft from ERP, CRM, or HR databases.
- If anyone has experience or other perspectives on this, always welcome (applies to everything I write here, of course)
Wire:
- Swiss messenger and video conferencing app, which despite the manageable team (about 100 employees) is now reportedly used by around 1800 organizations, including the German Bundestag, Interior Ministry, as well as BASF, EY, Orange, and Lidl
- In fact, the product is approved by the BSI for communication up to the classification VS-NfD. However, there is no Common Criteria certification yet.
- The Schwarz Group has invested, the platform will soon be moved from AWS to StackIt
- For customers, operation on-prem, in a private cloud, or as SaaS is possible
- E2E encryption is clear, admins or Wire itself cannot read the data, private keys are stored only on the users’ devices, self-deleting content is also deleted from the backend
- Uses the Message Layer Security (MLS) protocol => Authentication of device + user
- Users without accounts can be invited as guests to conferences
- Budget indication SaaS for a customer with 5000 users ~300k EUR/year => For most companies probably more interesting as a complement to Teams/Zoom to, e.g., secure communication of board members and supervisory board members.
- I always find it nice when a European company is so successful. The contacts also made a sympathetic impression, not arrogant.
SlashNext:
- Mail filter specialized in spear phishing / business email compromise (e.g., also as an add-on for Microsoft Defender for Office, Proofpoint, Barracuda, Mimecast)
- Founded by the former FireEye head for email protection
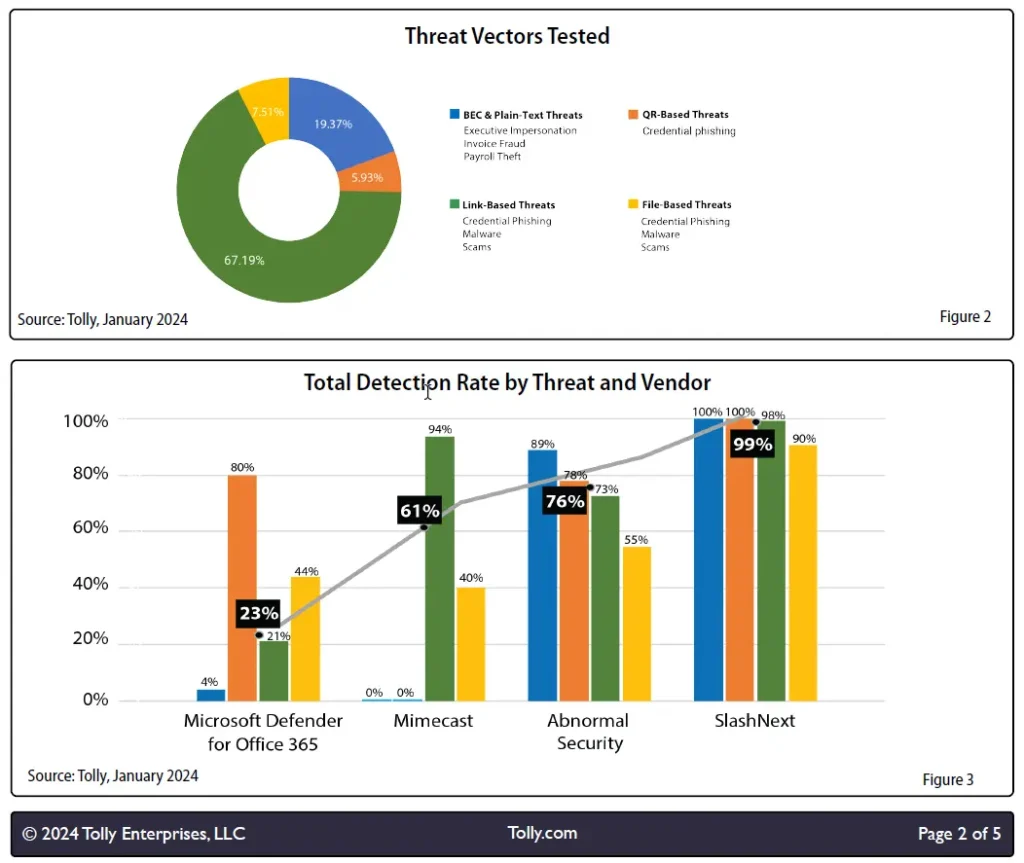
- I was initially naively happy: finally, a test result of effectiveness from an independent lab was provided, see the picture below, test report gladly forwarded upon request. Proofpoint or Cofense, for example, also advertise with better detection than Microsoft but without having it independently verified.
- Unfortunately, the test is neither fair nor meaningful in my view: The mail samples were mostly selected by SlashNext (so probably tested beforehand – an advantage the other providers did not have) and a recommended security feature was disabled at Microsoft (completion of URL scanning before forwarding to the mailbox). At least this is transparently stated in the lab’s test report, but the hint does not appear in the marketing material anymore. Surely an oversight.
- My written inquiry about this has not been answered yet
- About 150 corporate customers (e.g., DXC, Mattel) with a total of about 180,000 mailboxes
- No customers for the email product with headquarters in the EU yet, analysis of customer data on AWS instance in the USA
- Also offer an enterprise browser and a mobile threat protection product (SMishing)
By the way, one of my best qualities is to pass off other people’s work as my own to appear more diligent and smarter on the outside. Today, I’ll make an exception: Our colleague Rebecca Hundschell helped review the NIS-2 draft, and CyberCompagnon Philipp Pelkmann censored proofread the market commentary as always before sending it out.
As always, questions, suggestions, comments, experiences, and even opposing opinions or corrections are welcome by email.
Best regards
Jannis Stemmann
The Marktkommentar by Jannis Stemmann
Subscribe to Marktkommentar.
Gain More Insights Early On.
Marktkommentar includes insights from discussions with providers and customers on security projects and vendor briefings, questions and selective observations as well as unpopular theses in the security community.






