Hello everyone
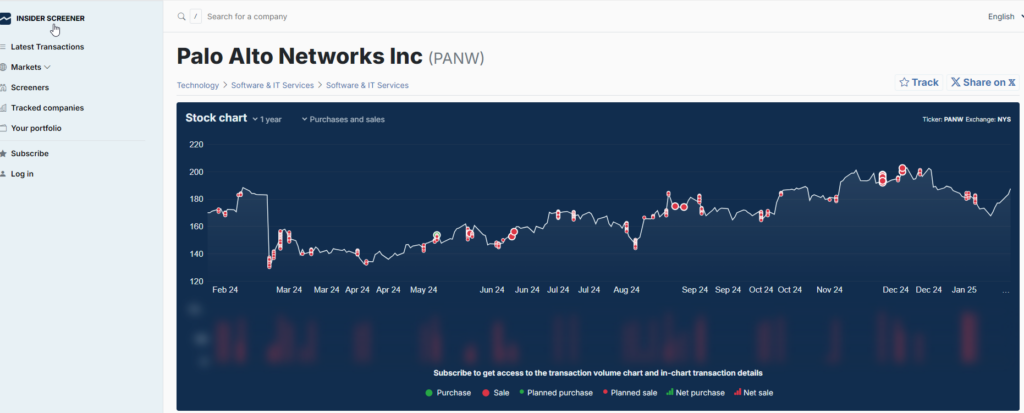
the CEO of Palo Alto Networks has sold shares of his employer for a total of ~USD 140 million in recent weeks (see chart attached). Certainly because he also regularly reads 😉 this market commentary. Or perhaps he is worried about the impending dismantling of cybersecurity legislation in the USA. In any case, the insider transactions, whether at Fortinet, Crowdstrike, Zscaler, Okta, Cisco, Cloudflare, SentinelOne or Rubrik, all look the same in the last 12 months: Obviously, there is more skepticism in the boardroom about the further price development than the investor relations presentations would suggest.
Thoma Bravo also wants to cash in with the first cybersecurity IPO of the year, namely at Sailpoint (Identity Security Suite incl. IGA and PAM). Sailpoint was previously listed on the stock exchange and was then taken over in 2016 for about USD 7 billion. We have taken a look at the stock exchange prospectus:
- Turnover approx. 700 million USD/year, approx. 3000 customers, approx. 2600 employees
- Not profitable (free cash flow also negative)
- Marketing & sales expenses of approx. 66% of sales with generously designed 30% sales growth. So again for the record: This single cybersecurity company spends half a billion on advertising, sales staff and sales commissions for resellers. Probably because the product sells itself, so to speak.
- “We operate in a highly competitive market” – IBM, Microsoft, Oracle, CyberArk, Okta and One Identity are named as competitors (and of course there are also some others such as Delinea, BeyondTrust, Ping or Savyint)
- The market for identity security is estimated at ~55 billion USD, which would be about 25% of the total market for cybersecurity worldwide = > may seem too high, after all, there are enough other categories
- As is usual after private equity transactions, Sailpoint is now slightly over-indebted (with about 2 times the turnover), the interest burden is about as high as the development expenses
The inclined readers already suspect it: Personally, I would never invest in such a situation as a small investor. So with my track record, it can be assumed that the IPO is guaranteed to be a huge success.
The EDR Telemetry Project continues to make progress and has published the Linux results. In addition to Uptycs, SentinelOne, MS Defender, Crowdstrike and LimaCharlie performed best. So far, ESET or VMWare Carbon Black, among others, have been beaten. Not recognized by most of the solutions in the test, among others:
- User Logoff and Failed Logons
- Scripts
- Newly created or changed user accounts
- New Drivers and Kernel/eBPF Events
- Service Deletion
So prove the need for XDR/SIEM solutions (or special Linux EDR variants) to achieve a comparable level of monitoring for Linux systems as for Windows machines. Here, too, however, further technical progress is certainly to be expected.
A few points from the internal Google SOC (“Detection & Response”) team responsible for monitoring GCP and workplaces of > 180k MA:
- For each internal asset, a risk analysis is carried out with the asset owner and, based on this, the detection rules are then assigned (or newly created).
- The detection rules are written and maintained by the same SOC analysts, who then (must) react to the incidents – to avoid alarms not being taken seriously
- The performance of the SOC is measured using the following KPIs, among others:
- Dwell time of detected attacks, currently probably at “a few hours”
- Cost per ticket
- Time to Resolution
- Number of events analyzed
- AI is used to generate and enrich the alerts, to automate case processing, to make recommendations for action, and to draft executive summaries/reports. The AI system learns from the remaining manual activities of the analysts
- All SOC analysts can analyze code, code well, and fully cover steps up to incident response, i.e., tend to have a low division of labor and few handoffs between teams or team members, but rather E2E case handling
And while we’re on the subject of detection engineering : The real professionals in this field are apparently the manufacturers of computer games like Call of Duty, who have to recognize sophisticated cheats of players and operate an EDR engine integrated into the game for this purpose. Keywords such as Windows API hooking, detection of test modes/debugging tools on the computer and monitoring of network traffic.
What’s new from the M&A scene?
- SoftwareOne has acquired Crayon from Norway – together the two resellers will have approx. 13k employees and move ~1.6 billion EUR in sales
- NinjaOne (Endpunkt-Mgmt.) has created Dropsuite (Cloud Data Backups & Recovery)
- Withsecure has sold its consulting business (approx. 250 employees) to the Swedish PE firm Neqst – the business was valued at ~EUR 23 million in the transaction => would guess, this corresponds to less than the annual turnover
- Tenable wants to acquire Vulcan (aggregation of vulnerabilities + asset data from multiple sources)
And with that, as usual, a few notes from vendor briefings:
CSOC (Certified Security Operations Center, Teil des TÜV Trust IT Verbunds):
- German SOC operator
- 24/7 monitoring via small shift teams
- Interesting: Complete tech stack (also for the employee PCs) only open source or in-house developments, i.e., zero Microsoft. Wazuh as SIEM.
- Also own AI tool to support SOC analysts => estimate in the interview was that the analysts work ~50% more productively as a result
- Many customers also with OT, e.g. municipal utilities. Own OT anomaly detection system as an alternative to Dragos, Claroty, Nozomi, Rhebo etc.
- Very transparent: Prices on homepage, e.g. monitoring of almost 1000 endpoints ~36 thousand EUR/a
Armo:
- Cloud Security from Israel, are known in the community for Kubescape (Kubernetes Security, alternative to Falco)
- Of course based on eBPF kernel monitoring
- Modules to shine at this point with a few shortcuts:
- CWPP (Cloud Workload Protection)
- CSPM/KSPM (Cloud/Kubernetes Security Posture Mgmt.)
- CADR (Cloud Application Detection and Response)
- CIEM (Cloud Infrastructure Entitlement Mgmt.)
- RBVM (Runtime Vulnerabilities Mgmt.)
- Infrastructure as Code Security
- API Security
- So they already cover a large part of the functions of Wiz or PAN Prisma today. But not yet or not to a comparable extent: Code Scanning (SAST/DAST). Instead, the strong focus on containers + K8s
- Deployment as SaaS, on prem or private cloud possible
- Approx. 50 customers, in the EU including Ericsson, Orange
Cork:
- Something very special: A kind of cyber insurance that is resold to end customers by MSP/MSSPs
- Cork offers a compensation payment of up to 500k USD in case a customer of this MSSP is hacked, i.e. a “breach warranty”. This also applies to minor damage such as voucher fraud, i.e. not only in the case of an extensive ransomware incident.
- The technical requirements that Cork requires from end customers are manageable:
- Backups
- EDR
- MFA (insb. Windows-Login)
- The breach warranty is supplemented by the preventive monitoring of the security tools used by MSSP and customers via APIs
- This makes it easier for companies as end customers to meet the requirements of conventional cyber insurance and at the same time (at least partially) compensate for the deductible in the event of a claim
- So far, it has only been active in the USA and focuses on SMEs in the end customer segment. Hiscox takes over the reinsurance
- In my opinion, the same concept would certainly be well received in Europe. 95% of the ~150 SOC and MDR providers operating in the DACH region do not yet offer a breach warranty => Still well suited as a differentiating feature
XM Cyber (Update):
- I assume that everyone in the DACH region knows (also through the intensive support of the Schwarz Group in the go-to-market) as a provider of CTEM/Attack Path Simulation based on CTEM/Attack Path Simulation (based on agents on the endpoints, a digital configuration twin is built in the cloud, which is then used for simulation, there are no scans or exploits in the production system). All possible attack paths are evaluated according to effort from the attacker’s point of view, among other things, in order to prioritize countermeasures at “choke points”. Therefore, here are just a few points that were interesting for me in the last technical deep dive:
- The number of ~300-400 was mentioned as a worldwide customer base, including SAP, Sana Group
- Consideration not only of vulnerabilities including misconfigurations, but also e.g. possible circumvention of EDR or already existing credentials
- The exploitability assessment takes into account existing libraries, but not whether the component was actually loaded into memory and executed on that host
- The remediation recommendations for action such as patches or changes to registry keys (some of which were really very detailed including screenshots for e.g. GPO adjustments) can be transferred directly to an ITSM or SOAR
- Customers must create individual scenarios for the on-prem assets (esp. Breach Points and Critical Assets). Why can’t you just automatically extend the scope to the entire company and all assets as possible breach points and target systems? Because then there is no more prioritization. For very large environments with many legal entities and networks, this may be time-consuming and requires prioritization as input information. However, scenario-independent analyses are probably on the roadmap.
- Vulnerabilities found can be specifically excluded as an accepted risk for further prioritization (e.g. if a measure has already been determined). At the level of attack techniques, however, this probably only works to a limited extent.
- With IaaS/PaaS, an API key is also sufficient to get all the information (so no agent installation necessary). Doesn’t work for SaaS apps yet
- Customer data can also be encrypted via the new Google cooperation in such a way that XM Cyber does not have access to it
- Attack paths via OT, Enterprise IoT devices and hypervisors can be mapped at least partially via the integration of vulnerability scan data (via Tenable, Qualys or similar)
As always: Questions, suggestions, comments, experience reports and also opposing opinions or corrections are welcome by email. Ditto for unsubscribing from the mailing list.
For the people who are reading this email for the first time: Congratulations! If you are interested, you can register here.
Regards
Jannis Stemmann






