Compare Security Information and Event Management (SIEM)
Looking For A
Security Information and Event Management Solution?
SIEM Providers
Compare SIEM With Us - The Vendors on the Market

A Look at the Market
SIEM Market Trends
Reduce false positive alerts with advanced ML models
Prevent unhandled incidents with AI and response automation e.g., via convergence with XDR solutions
Leverage Generative AI for natural language searches, rule development or remediation plan generation
De-Couple Data Lake from proprietary SIEM solution and do not separate security from business data
Cybersecurity Basics
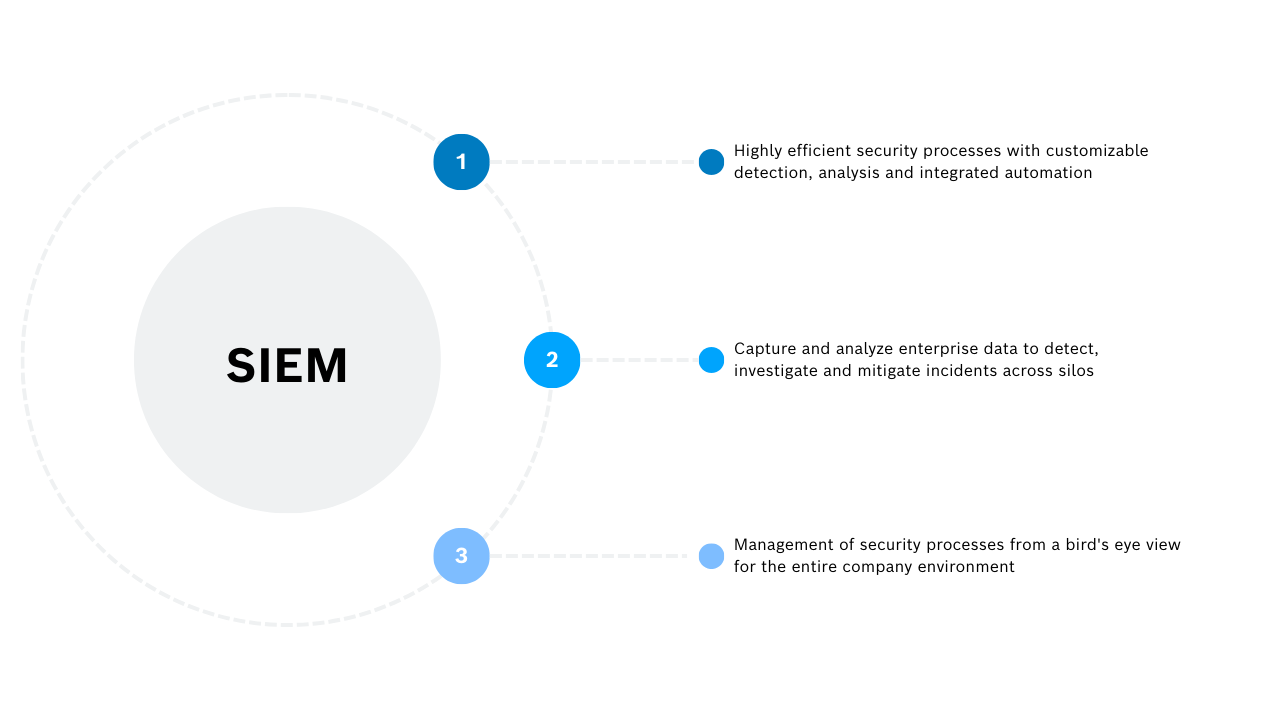
What Is a SIEM?
A SIEM (Security Information and Event Management) system helps companies detect, analyze and respond to security threats before they impact business operations. It collects log data from various sources such as servers, network devices or applications and detects suspicious activity by sorting and correlating event information, including a severity rating.
In addition, it enables historical analysis of security events to support incident investigation and generate compliance reports. In combination with SOAR (Security Orchestration, Automation, and Response) solutions, a SIEM system can automatically respond to suspicious activity.
A SIEM selection process can be complex. Costs and service levels vary significantly between providers. Take advantage of our experience and let us advise you. Enquire now to compare offers. We will help you to identify the right SIEM for your company’s individual requirements and needs.
SIMPLE. CLEAR. AFFORDABLE.
How We Help You Find the Right SIEM Provider
Target Definition Of The Future Concept
Target definition and development of the future concept in several workshops. This includes the target architecture (e.g. SIEM- vs. XDR-based) and the question of what is provided internally or outsourced (e.g. co-management of the SIEM solution).
Result: Defined procedure/objective for the tendering of the target scenario
Tender Preparation & Specifications
Workshops to record the requirements (scoping) and iterative adaptation of the specifications after consultation and clarification of open questions
Result:
- Specification of an anonymized specification sheet for the tender/comparison of offers
- Selection of a longlist of 5 providers for the invitation to tender
Offer Comparison & Decision Preparation
Request for tenders from defined providers – can be anonymized
Coordination, consolidation and preparation of the offers as well as evaluation with a recommendation regarding top providers and concepts in comparison with the specification and the target concept
Creation of a report with a clear award recommendation & visibility of the differentiating features
Result: Basis for a qualitative decision for 1-2 providers for final negotiation and awarding of contract
Optional
Support With Commercial And Legal Contract Negotiations
Result: Signed contract with 1 provider
Optional
Support With Onboarding The Solution
Result: Productive SIEM service as part of the coordinated onboarding plan
Optional
360° Inventory And Market Study
Part 1: Inventory & diagnostics
Part 2: Overview of the market and derivation of a strategy
Result: Decision on a suitable solution and procedure for SIEM selection
VALUABLE INSIGHTS FROM OUR EXPERT
All About SIEM vs. XDR With Patrick Eberle
WHITEPAPER
Three possible SIEM solutions for your external managed SOC
When choosing the right managed soc partner, the question of how to handle security information and event management (SIEM) is of central significance.
In this whitepaper, we will show you three variants with advantages and disadvantages, and also explain to you how and why our customers choose which SIEM variant.


Your Expert for Questions -
Get Answers Here
Jannis Stemmann
CEO CyberCompare
+49 (0)711 811-91494
Compare CYBERSECURITY SOLUTIONS WITH US
Not Looking For SIEM Solutions?
Compare Other Solutions & Services With Us
Compare SOC Provider With Us
You Can Receive Offers From the Following Providers - And All Others
At CyberCompare, we help you find the right Security Operations Center for your company in a resource-efficient way, so you can ensure the security and availability of your systems and data. With us, the large field of cybersecurity becomes manageable for you. You can get an initial overview of possible SOCs in our provider directory.