Hello everyone,
“In preparing for battle I have always found that plans are useless, but planning is indispensable,” said Dwight Eisenhower (General and President of the USA). To a large extent, this also applies to Threat & Risk Analyses (TARA): While the heat maps and spreadsheets per se are not constantly used as a reference work or can fend off attacks themselves like cool tools, the added value lies in carefully thinking through the possible “what could go wrong” scenarios. Similar to emergency plans, the secret to risk analyses obviously lies in the level of detail: Too generic = > Useless paper; too detailed => script with 1000 pages, already outdated on day 1.
In my perception, risk analyses occupy the same place in the security world as failure mode & effect analyses (FMEA) do for engineers:
- Unpopular as a work task
- Theoretical paper monsters
- Exhausting team discussions among opinionated experts about irrelevant details (“Is the probability of occurrence 0.01% or 0.05%)?
- Lots of embarrassing questions à la “Why didn’t you think about it earlier?”
- A bunch of tasks in the aftermath
- Guaranteed fun-free
- And at the same time unbeaten at cost-effectively preventing problems
FMEAs are developed during development, production or other steps in the life cycle and serve to anticipate possible problems in design and manufacturing processes and to incorporate changes in design or manufacturing in good time. The results are the basis for simulation and test plans. Of course, the whole thing has to be updated with every product change and new problems (e.g. a customer complaint). Sound familiar?
Lame or casual: However, the importance of risk and threat analyses could be better. We all love to be the heroic and ingenious Savior1 , freeing the rest of the organization from insoluble dilemmas at the last second. And we admire the real HackerHackers, who somehow manage to trick our SOC. Pen testers, red teamers, incident responders, firefighters: Exciting jobs, permanently in spicy mode of life.
For the cellar children, on the other hand, who have added a line in the risk analysis or meticulously worked through a task in the OPL after several days of mental exercises, there is usually no applause (or only applause that is donated because it is good for the team culture and someone is watching). As is usually the case in life, the willingness to pay for prevention is lower than for therapy. These mostly pale-faced colleagues and their Excel wallpapers have probably prevented just as many security fires as the aforementioned job profiles.
In line with this plea for risk analyses and analysts, a practical example of the TARA of a production network (incl. servers, PLC, MES) comes from the VDMA, still freely available. Excellently done, with ~50 threat scenarios according to MITRE ATT&CK and STRIDE categories, each assessed according to IEC 62443. Top 1 risk mitigation measure in the (presumably real-life example) was network segmentation, followed by Privileged Account Mgmt.
Clorox is suing managed service provider Cognizant for $380 million in damages for negligently providing criminals with access to Clorox’s systems that led to a major incident.
- Cognizant did not carry out an identity check, a call to the service desk was enough for the attackers to get user accounts including passwords and MFA reset.
- The indictment contains recordings of telephone conversations on the subject:
-
- Cybercriminal: I don’t have a password, so I can’t connect.
- Cognizant Agent: Oh, ok. Ok. So let me provide the password to you ok?
- Cybercriminal: Alright. Yep. Yeah, what’s the password?
- Cognizant Agent: Just a minute. So it starts with the word “Welcome…”
- The damages claimed are equivalent to approximately 5% of Clorox’s annual revenue or roundabout’s profits for an average year. From the annual report : “We quickly restored operations, fully rebuilt supply and distribution, and recovered the vast majority of the market share we lost from the cyberattack.”
- The service provider does not seem to be entirely happy with the accusations, from the official PR statement: “It is shocking that a corporation the size of Clorox had such an inept internal cybersecurity system to mitigate this attack.”
Very readable article by an incident handler at a US bank on differences in incident analysis between on-prem and AWS EC2 VM environments (representing Cloud Compute instances), read time ~15 min.
Examples from it:
- With AWS, attackers do not need exploits for privilege escalation, but usually the Associated IAM Role + API Calls are sufficient
- Data exfiltration does not necessarily appear in the VPC flow logs, but can be done fastest + without a trace via S3 copies.
Microsoft is making the bundle even more attractive: From now on, Defender Threat Intelligence (once taken over by RiskIQ ) is now included for all Defender customers at no additional cost.
List prices were easily in the five-digit range – but the number of customers could be counted on one hand.
Consolidation in the security market: 200 providers became 11 (see graphic from Ventures in Security) – fortunately, there are ~7000 others.
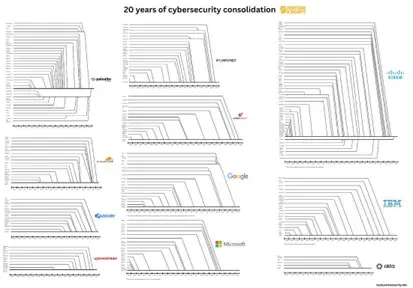
The best business model in the security market is probably not to sell firewalls after all. But to found a startup (or to invest in one early) and then the quick exit to an astronomical multiple on one of the “platforms”.
If you are planning to do just that, or know someone who is planning to: Feel free to contact me. We are currently looking for medium-sized security companies (ideally 25-75 employees) in the areas of GRC, SOC and consulting on behalf of a European investor.
So then the transition to the noteworthy M&A News:
- SentinelOne buys Prompt Security for $250 million: Quasi an EDR for AI, including discovery of AI applications, corporate policy setting, detection and blocking of attacks such as prompt injection, and MCP gateway functionality
- Network Monitoring + ZTNA Provider Netbrain Technologies Goes to Blackstone for 750 Million
- SecurityBridge further expands the SAP security portfolio with Cybersafe (SSO for SAP)
- KnowBe4 raises another USD 1.5 billion via the bond market. The awareness/phishing leader went to Vista Equity a few years ago for just under $5 billion
Notes from vendor conversations:
Sophos (Update):
- I wanted to see how far the integration with Secureworks has progressed
- Secureworks is/was an MSSP with its own XDR solution (“Taegis” platform) and had a strong customer base in the US, on average significantly larger number of endpoints than Sophos’ MDR customers (an impressive ~35,000, of course relatively few in the enterprise segment)
- Secureworks Taegis is probably best described as an XDR-based MDR service:
-
- EDR + log/event data collectors (with many native connectors), the whole thing then correlates and analyzed in the cloud. The history is interesting: Originally it was a SIEM, the EDR function came later (i.e. the other way around as with almost all other XDR manufacturers)
- With MDR, which not only analyzes EDR events, but all connected log sources
- Cool feature: “Ask an Expert” in the console with 90 seconds guaranteed response time of a human analyst. Very refreshing in the whole AI chatbot world
- Shift model for analysts, most for EU clients are based in Romania (not follow the sun)
- Currently, the only technical change is that the Sophos AV/EPP agent is integrated into Taegis as well as alternatively Crowdstrike, SentinelOne, Defender, etc. Depending on the risk profile and complexity, customers are recommended to use either the Sophos or Taegis MDR.
- Unfortunately, the Sophos MDR Breach Warranty does not yet apply to Taegis MDR
- The next step on the roadmap will then be the Sophos Email, ITDR, integration.
- A unified XDR solution with only 1 MDR service for all customers is expected to be available in 1 year. The data lake is to come from Taegis, but the UI and EPP from Sophos
- The Sophos MDR service can also be booked purely on the basis of MS Defender (without Sophos or Taegis EDR)
- Licensing based on endpoints (despite log data monitoring), which can be attractive
- An incident response retainer including onsite assignments can also be booked separately
Whalebone:
- Czech provider of Secure DNS (cloud or on prem resolver), on the market for about 9 years, main competitor Cisco (Umbrella), but also WAF providers such as Cloudflare, Fastly or Akamai
- Approx. 500 customers, clear focus on telcos, ISPs and authorities (including Telefonica / O2), but smallest customer has only 20 MA
- Infrastructure and MA exclusively in the EU
- The most important feature is the block or warning of malicious domains directly when the URL query is resolved (before connection is established) based on an allow/deny list that is as up-to-date as possible
- That’s why we have our own Threat Intel team, which adjusts the algorithm for scoring the trustworthiness of domains
- In addition, included functions such as automated dark web surgeries for leaked credentials that are related to one’s own domain
- Prices approx. 15-20 EUR/user/year (not depending on the number of devices)
Prim’X:
- French provider of encryption, active for ~20 years, approx. 60 MA
- Competitors to Thales, Rohde & Schwarz, Secunet and of course also e.g. Microsoft (Thales itself is probably a PrimX customer)
- Customers esp. larger companies (e.g. Orange) and public. Institutions (e.g. NATO and EU, approved up to VS-Nfd / “Restricted”, which is the lowest level of confidentiality)
- EAL3+ Common Criteria certified
- Architecture: Client-side encryption, each user has its own key (e.g. hardware token or certificate)
- Works for local data, network shares, M365 or other email clients
- Treat for email encryption (ZED / ZEDMAIL): Recipients can reply encrypted without being a customer of PrimX. This is also the killer feature with e.g. Cryptshare.
- Still looking for resellers in the DACH region
StrongDM:
- PAM solution from USA
- Unique selling point: Just-in-time access control to databases, Slack or Teams resources, among others
- Founded 10 years ago, ~250 customers (including Pepsi, SentinelOne, but also many smaller ones), including EU/DACH
- Hybrid architecture: SaaS Engine + on prem gateway (1 gateway can control ~5000 parallel sessions)
- Works with many secret vaults (Hashivault, AWS Secrets Manager, Azure Key Store, CyberArk, Delinea…) and of course the common IdPs
- Session recording + logging, incl. database queries
- Pricing based on number of users
- Still looking for channel partners in the DACH region
So, that’s it for this time. As always, questions, suggestions, comments, experience reports, topic requests and also opposing opinions or corrections are welcome by email. Ditto for unsubscribing from the mailing list.
For the people who have received the market commentary for the first time: Here you can register if you are interested or make a backup of the archive.
Best regards
Jannis Stemmann






