Hello everyone,
Wiz was actually founded only about 4 ½ years ago (thanks for the heads-up, Georg!). So, regardless of how and at what valuation the exit occurs, achieving ~1 billion in revenue is an incredible accomplishment.
However, there has been some criticism recently regarding how these customers were acquired—I’ll need to take a closer look at that.
Otherwise, today is all about OT Security for a change. If you’re not interested in OT or don’t deal with it, feel free to browse elsewhere (for example, the Crowdstrike incident has generated a lot of reading material. Fortunately, it seems that we now have almost as many security experts in the population as we do millions of football professionals 😉).
Waterfall (more about the provider below) released an interesting 2024 Threat Report – OT Cyberattacks with Physical Consequences a few weeks ago.
Even more interesting was Dale Peterson’s conversation with the main author, Andrew Ginter, about it. Some key takeaways:
- The report is based on 68 known security incidents worldwide in 2023 that had verifiable consequences in physical processes (i.e., not just data theft/encryption, but also impacts like production outages or equipment damage).
- In most of these cases, the responsible parties shut down processes in the OT to reduce or eliminate the risk of infection (“Abundance of Caution” in the SEC filings). Colonial Pipelines is an example of this—not the payment system failure, which was reported in the press at one time.
- In 12 attacks, however, the OT was directly affected. For example: planes in Israel and Egypt disrupted by GPS jammers in navigation, or Iranian gas stations that were incapacitated.
- Of course, there is a dark figure of unreported incidents—but the authors believe that the report covers more than half of all actual attacks.
- Also, no incidents at hospitals/clinics were considered, for whatever reason.
- There still seem to be almost no known attacks where OT automation technology in companies was successfully compromised. This is not only evident from the above report but also from other statements:
- In the podcast conversation with Klaus Mochalski (founder and CEO of Rhebo), Stefan Grützmacher (Städtische Werke AG and on the advisory board of Rhebo) states that he has not observed any OT incidents so far.
- Götz Schartner from 8Com (Managed SOC operator, approx. 70% of customers with OT in scope) confirms the same: so far, exactly zero OT-specific attacks have been observed.
- I would assume that Rhebo, as one of the leading providers of OT anomaly detection systems, would have a business interest in claiming the opposite. So, big respect to Klaus and his interview partners for this honesty! And to be fair, anomaly detection offers significant advantages in optimization and troubleshooting for operations teams in power plants, refineries, etc., thereby increasing availability.
- Integration specialists for IRMA (another OT anomaly detection system, commonly used by water utilities) have also confirmed that they have never detected a single attack on OT automation technology in their many years of practice. You would think this statement might harm their business.
- Conclusion for me as of today:
- OT Security Basics such as securing remote access, network segmentation, and emergency exercises are an absolute must.
- Complex systems for monitoring OT protocols for network anomalies, on the other hand, seem questionable for most customers, at least for detecting external cyberattacks. Because there simply are no attacks on industrial controls that could be detected this way. For attackers, there are much simpler ways to extort money—even in OT. Could this change someday? Theoretically, yes, but at the moment, the next euro could probably be better spent elsewhere.
- Kudos to Ralph Langner (OTbase), who repeatedly points out these facts instead of profiting from scaremongering—something that would surely be easy for him to do, after all, he was one of those who decrypted Stuxnet.
- If anyone has other reliable data points on this, feel free to share them.
Here are some notes from vendor meetings:
Denexus:
- Cyber Risk Quantification (=Board Level summaries and progress reports, in which all information is management-friendly summarized in EUR figures) for OT Security risks.
- I was familiar with this for IT security (e.g., Safe, Squalify, Axio, Panaseer), but not yet for OT.
- ~200 customer installations, also in the EU, especially in energy/oil+gas (e.g., Repsol, edf).
- Uses external + internal vulnerability scans, manually inputted information on measures, and insurance data to quantify OT cyber risks according to the FAIR method.
- The so-called Attack Path Mapping for assessing the likelihood of occurrence sounds interesting at first but turns out to be a generic assignment of Initial Access steps (like “Phishing”) to Impact (like “Downtime”). A customer-specific modeling or validation at the technical network level does not seem to have any influence.
- Therefore, it is theoretically well-suited for creating reports for risk management and calculating or justifying the ROI for further security measures. Thus, it’s probably something for publicly traded companies.
- The danger, in my view, lies in a false sense of accuracy—I am not aware of any actual data from insurers/reinsurers that can predict the success probability of an attack based on the security measures implemented. Because an attacker could possibly choose an alternative path—who knows if that wouldn’t work as well. Especially with OT-specific measures like an OT NIDS or OT network segmentation, the data seems thin.
- As with the above tools for IT, no data on the costs of implementing additional security measures such as tools, services, or processes are included.
Waterfall Security (Update):
- We know them from the “Data Diodes”:
- Commonly used especially in critical infrastructure (nuclear power plants, banks, process control system manufacturers).
- Unidirectional gateways based on laser and photocell, i.e., in normal operation, physical separation in one direction, L1 connection in the other direction, no TCP/IP connection between IT and OT possible.
- For interactions with enterprise IT (e.g., connection to ERP), a “Digital Twin” is created as a replica of the SCADA system and OT servers.
- However, the OT server infrastructure must be duplicated by the customer, for lean protocols like Syslog and OPC-DA, the digital twin runs directly on the gateway.
- Disadvantage: the digital twin must still be equipped with a firewall, AV, etc., just like a DMZ.
- Software updates (e.g., AV) or other accesses to the real OT system are done via a bypass that can be unlocked using a key switch.
- There was a briefing on the new remote access solution (Hardware Enforced Remote Access HERA):
- Basically a data diode that only transmits encrypted video data (screen capture) from OT to IT.
- Combined with a parallel data diode that only transmits encrypted keyboard and mouse data from IT to OT.
- Therefore, it can be used for real-time changes to program parameters or configurations.
- Common Criteria EAL4+ certified.
- Usual features like MFA, session recording, logging, multi-site management, etc.
- Disadvantage: Of course, it’s not usable for many remote access applications (e.g., transferring PLC programs) and is likely quite expensive if access is to be granular to individual assets/segments.
- The main cost driver is the number of user clients (i.e., the number of maintenance technicians with access, which can potentially be consolidated via jump hosts).
- In reality, there’s also the limitation of connected services via the bandwidth of the gateways.
- Worth checking out—the DACH area manager is a true tech enthusiast, so a conversation is definitely worthwhile.
XAGE:
- Remote Access (though they call it Zero Trust) for IT/OT environments.
- Distributed network of containers (“Nodes”) or hardware gateways in the customer environment that, as I understand it, establish IPSec tunnels and encapsulate industrial protocols in them. Therefore, the tunnel does not end directly at a PLC but at a node in a zone classified as secure.
- Each node contains all policies for access rights, so the system also works without an internet connection or in the event of a central policy engine failure.
- Surprisingly, it is also IEC 62443-4-1 certified, in addition to FIPS 140-2.
- In the conversation, I also learned that Gartner now (again) refers to OT as “Cyber-Physical Systems” / CPS.
Fortiphyd:
- Yes, that’s really their name, but they have nothing to do with Fortinet. A small startup from the USA.
- Very innovative but also very specialized solution: Anti-malware for PLCs or PLC/RTU (“Controller Endpoint Detection and Response”), i.e., OT/IIoT security.
- The AV software is programmed in the same languages as the control logic programs running on the PLCs (ladder logic, structured text, IEC 61131).
- Besides the AV “agent” on each controller, a central server for monitoring is needed.
- However, implementation is likely to face high hurdles: it has to be adapted for each controller type, and then functionality (e.g., runtimes, especially in real-time!) needs to be tested. Therefore, OEMs of automation technology and plant builders seem like more suitable customers than operators.
- Interestingly, Nozomi introduced an OEM-specific solution for Mitsubishi’s PLCs this week (Arc), which is based on the same approach.
Network Perception:
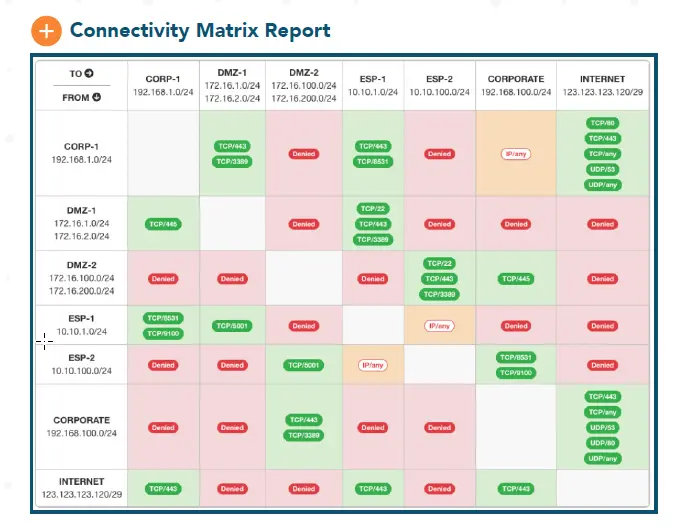
- A small US provider with a smart solution for OT network discovery, attack path visualization, and firewall rule checking (i.e., no anomaly detection à la Nozomi or Claroty), works with all common firewalls.
- Clear focus on the energy sector, though no customers in the EU yet.
- Cool feature, as I found: automatic display of a matrix of network segments (=> which network segments can communicate with which other segments through which ports), see the attached image.
As always, questions, suggestions, comments, experience reports, and even opposing opinions or corrections are welcome via email.
Best regards,
Jannis Stemman
The Marktkommentar by Jannis Stemmann
Subscribe to Marktkommentar.
Gain More Insights Early On.
Marktkommentar includes insights from discussions with providers and customers on security projects and vendor briefings, questions and selective observations as well as unpopular theses in the security community.







