Hello everyone,
Rubrik is going public – we took a look at the IPO prospectus. Of 3100 employees, 1300 work in marketing and sales, i.e. one in three.
On the one hand, an alarming number, on the other, significantly fewer than at Darktrace at the time of the IPO – two thirds of all employees. Then, of course, there are the legions of salespeople at the channel partners, which explains the > 70% expenditure on marketing and sales.
Here is a relatively recent analysis of listed security providers (source: annual reports, I am happy to provide raw data for review).
The expenditure for marketing+sales is shown in red, the expenditure for development in blue, in each case as a % of turnover in relation to the last 12 months for which the data was published. Example Tenable: A whopping 49% of turnover was spent on marketing+sales, and 19% on product development.
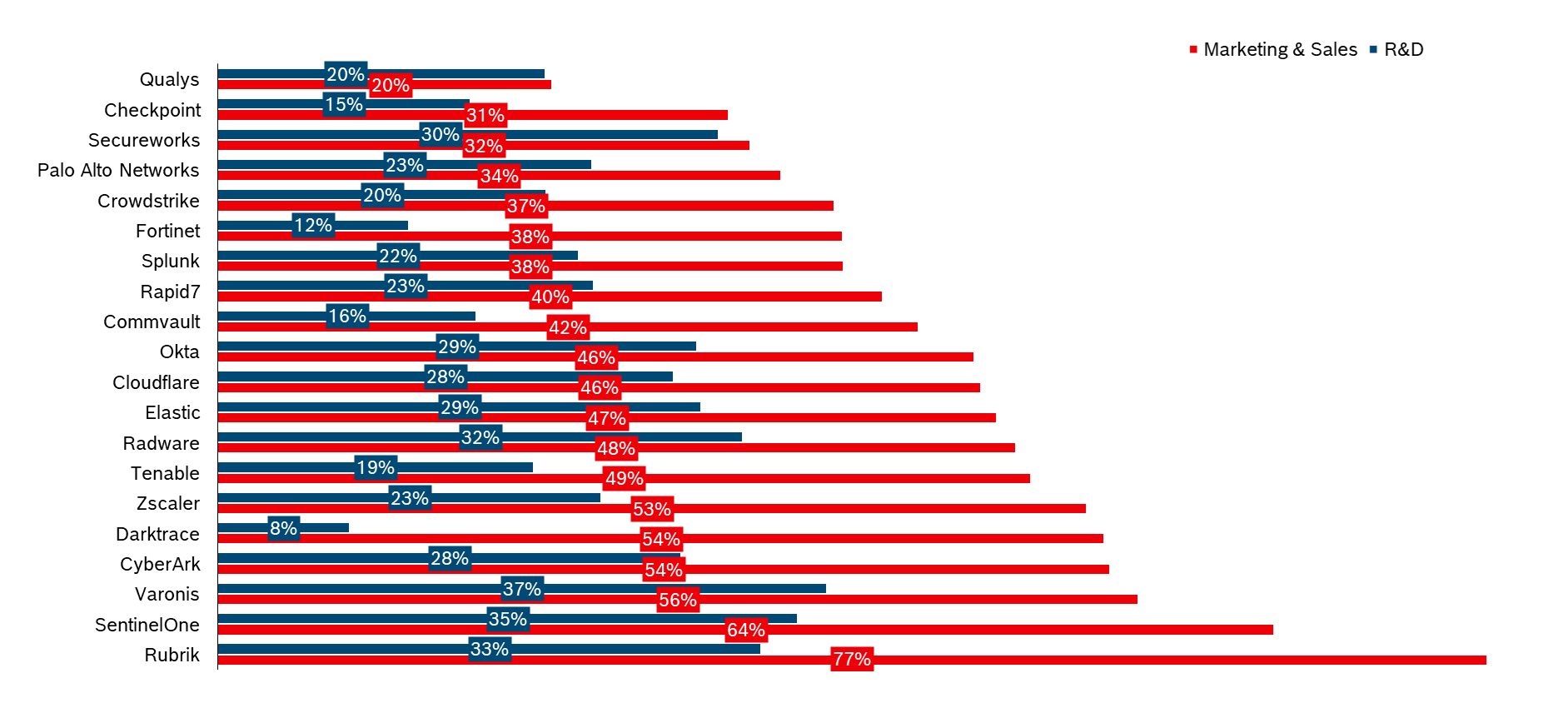
It can be seen that expenditure on marketing+sales exceeds investment in product development across the board.
I would tend to say that sales expenses are lower in percentage terms for large companies than for smaller ones. But even Splunk or Fortinet, after ~20 years on the market, still have to spend more than a third of their revenue on advertising and sales. A clear sign of the strong competition on the market. Otherwise, XM Cyber would probably not place any ads in my beloved Hamburg evening paper either, that’s almost an act of desperation 😉.
Who is missing from the list? Alongside private companies, of course, the giants in the industry that run security as a side business (especially Microsoft, Google, Cisco, IBM and players like Akamai). At least for me, there are no comparable figures for the security divisions, although Microsoft is of course approx. 3x the size of Palo Alto or approx. 8x the size of Crowdstrike with ~ USD 25 billion in security sales. Overall, however, it is striking: Marketing+Sales expenses are significantly lower if you don’t only offer security, and that doesn’t just apply to our favorite monopolist Microsoft.
A rough estimate as a somewhat provocative hypothesis:
- Global market for cybersecurity EUR 150-200 billion per year
- A third of this is consumed via the sales channel in the form of Google ads, whisky tasting events and sales commissions, for example, i.e. around EUR 50 billion
- There are an estimated 200,000 target companies and public bodies in the enterprise business globally (Gartner states that the TAM for their IT research is 180,000 customers)
- This means that around EUR 250 thousand per year is invested in advertising and sales staff for each target customer
Speaking of Darktrace, they are expected to be acquired by the private equity firm Thoma Bravo. This would be Thoma Bravo‘s 28th cybersecurity portfolio company (including Delinea, Entrust, Forgerock, Imprivata, Ping, Proofpoint and Sophos).
Let’s see whether this will eventually become a large integrated platform or whether the synergies will continue to be limited to sales. On a smaller scale, Istari is pursuing a similar approach (well-known names in the portfolio companies include Armis, BlueVoyant, Claroty and Sygnia).
And here are a few key points from discussions with providers:
- Data leakage protection / Data classification / Data Security Posture Management / Data Detection & Response (Wow! I heard the last term for the first time)
- Automatic classification so far only for cloud environments (but all platforms), on premise classification solution still in progress
- Allegedly high accuracy in classification due to many parameters used for classification (region, data type, context)
OASIS Security:
- “Non-human-identity management” => A type of privileged identity management (PIM) solution specifically for service accounts, service principals, API tokens, certificates and keys that are used for communication between applications (A2A, M2M)
- The solution automates the inventory of these identities, shows privileges, usage in applications (via logs), exposure and age, prioritizes conspicuous accounts and helps to resolve problems (generally rotation, revocation of rights, splitting the account or deleting the old token). The secrets themselves are not saved (again).
- Relevant problem, as incidents at Okta, Microsoft, Mercedes and Cloudflare show
- Customers include other major security players
- However, it seems to me that PAM systems such as CyberArk for DevSecOps or SSH PrivX already cover this to some extent. Smaller customers help themselves with scripts. If you only have a standard PAM with Secret Vault, OASIS is probably a good addition.
Narrowin:
- Microsegmentation and network discovery (both for IT and OT)
- Small Swiss company, founded in 2020, investment by EnBW
- Plug+Play firewall appliances based on embedded Linux, about the size of a fist. So no classic optocoupler data diode like Waterfall. Customers can also provide their own hardware.
- Trimmed for simplicity and cost (significantly cheaper than the segmentation FW of the established players): Per device and year (HW+SW) from 200-250 EUR
- Simplest policy: Controller can access network, but no external connection to endpoint possible
- Network mapping: Collection and harmonization of network connections and VLANs via routers, switches, etc.
- Passive assignment of endpoints to manufacturers such as Beckhoff, Siemens or similar via fingerprinting, but relatively superficial, i.e. no vulnerability management
- Checking the interface configurations, e.g. more than 2 MAC addresses behind a port
- Customers primarily in the area of critical infrastructures (hospitals, utilities)
As always: Questions, suggestions, comments, experience reports and also opposing opinions or corrections are welcome by email.
Best regards
Jannis Stemmann
The Marktkommentar by Jannis Stemmann
Subscribe to Marktkommentar.
Gain More Insights Early On.
Marktkommentar includes insights from discussions with providers and customers on security projects and vendor briefings, questions and selective observations as well as unpopular theses in the security community.







