Cybersecurity has been seen as an inefficient and non-transparent market: more than 7000 vendors, distributors, resellers, managed security service providers, and consultancies approach IT leaders with a similar message: “Buy my product or service (and buy it now), or you won’t be safe!”. But a key fact should be addressed: on average, between one-third and one-half of external spending on cybersecurity is spent on marketing and sales – money that could be better invested in product development. After all, who is paying for these sales and marketing teams? You as the customer. Of course, via detours and convoluted commission and bonus schemes.

On the customer/operator side, it is apparent that often overburdened IT teams have to be co-managed from securing existing infrastructure retrospectively to the fact that every new project in the company interacts with IT. Attackers are learning, and regulatory requirements are increasing. In addition, there is a “war of talent” across all areas and industries. The IT sector is also heavily affected, but if you look more closely, there is a need for more technical talent rather than sales talent.
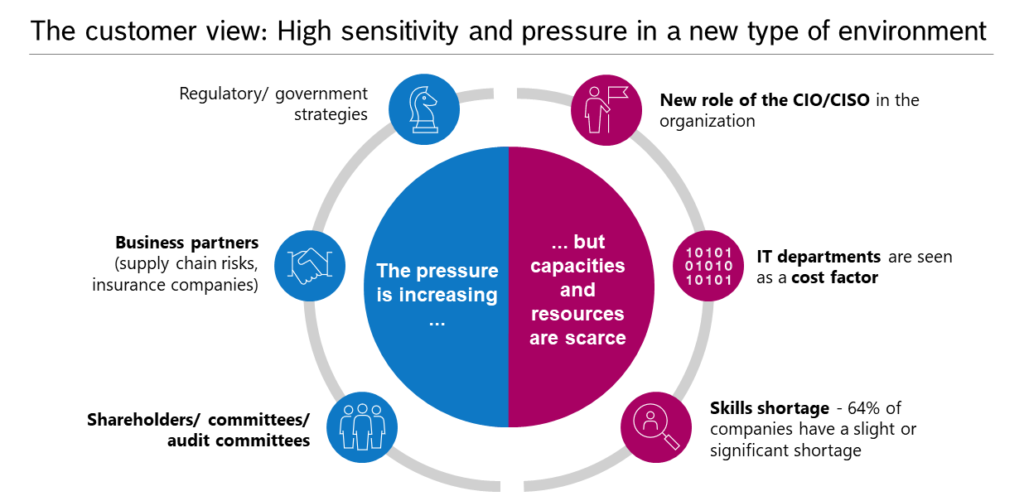
New acquisitions or tenders for security projects must be handled in addition to the already demanding day-to-day business.
In the following, five approaches are outlined to achieve the best possible price/performance ratio with reduced risk for procuring cybersecurity projects. The potential savings are considerable and, on average, far above what is expected in other categories.
Step 1: Prioritization
In many cases, the solution space is narrowed down to the question “Provider A or B”. But have the opportunity costs also been considered? For example, would it make more sense to hire an employee for the budget who could take care of the topic of security in a dedicated manner? Are there measures that would enable a similarly high gain in the level of protection for significantly less money?
An independent stocktaking helps here.
Step 2: Description of the requirements
Regardless of the specifications, or service description, ensure you don’t unnecessarily exclude any leading providers by using “knockout criteria”. For example, system houses have sales partnerships with certain vendors – the more the system house sells, the higher the margins on it. System houses are, therefore, generally not independent in their recommendations. At the same time, no unnecessary features or options should be defined – again, what could the budget be used for elsewhere, e.g., additional team resources?
It often makes more sense to expand a new solution step by step to keep learning and your team manageable. Managed services also involve intensive participation obligations, especially at the beginning, which will strain your colleagues.
Step 3: Inquiry with providers
The mistake is often made by requesting several offers from alternative manufacturers from the same system house or reseller. The problem with this is that the system house has then de facto excluded the competition by registering the deal with several manufacturers. You can request an alternative offer from the manufacturer via another channel partner as a customer. However, this partner will receive significantly worse conditions (discounts on list prices and bonuses/kickbacks) than the partner who registered the deal first. Reseller margins of 20 – 30% (and in some cases even higher margins) on the licenses are fixed. The lock-in typically extends to support services, which you can only obtain at a higher price from another reseller.
You will therefore be in a better negotiating position if you approach each manufacturer via a different sales partner – namely via a partner with the highest status in each case (“Gold”, “Preferred”, etc.) so that you can benefit from the best possible conditions.
It is also always advisable to separate consulting, implementation, and operation (i.e., purchasing services) from pure license purchasing for standard software such as AV, EDR, NDR, SIEM licenses or similar. From the current annual report of one of the largest system houses: “A customer who knows which contract model would be suitable and exactly how many standard software licenses he or she needs would not gain any added value from the pre-sales consulting.”
Of course, there are cases where intensive consulting is necessary – for example, in the development of individual backup concepts. But in many other projects, it’s just a matter of passing on offers. For example, the manufacturer pays the system house solely for customer access. As a customer, you can see the difference directly: Who explains the product to you in technical depth – the manufacturer’s pre-sales engineer or the system house’s consultant? In the case of many MDR services, it is now the manufacturer who monitors and operates for thousands of customers. It thus naturally has an enormous know-how advantage over the MSSPs.
Step 4: Technical and commercial comparison of offers
Are the offers comparable in the scope of services?
In some cases, we can see drastic differences in licensing terms, which can lead to significant savings opportunities: For example, there are providers of endpoint protection solutions where customers do not have to pay for thin clients with virtual desktop environments, but only a single license for the terminal server. For remote access solutions, some leading vendors do not charge an annual license fee (yes, they still exist) – others charge additional licenses per user. The number of development projects or scans for vulnerability management platforms can be critical. And for SIEM systems, it was and is common to charge based on log volume. In the meantime, however, some providers (also under pressure from XDR solutions) license according to the number of endpoints.
As an intermediate step from the evaluation on paper to proof of concept/value, a structured “test case demo” has often proven its worth. Here, test cases are agreed upon with the manufacturers, which are presented in a demo (2-3 hours) via video conference and evaluated by the customer. This makes it possible to achieve a significantly higher level of comparability and meaningfulness with little effort than with conventional marketing presentations.
Step 5: Negotiation
At this point, the manufacturer (via vendor manager, account manager or similar) and reseller/system house should be informed again that they are in a competitive situation. Of course, keeping at least two good candidates in the running is important until the final decision is made. It sounds like a truism but is often disregarded.
Manufacturers’ list prices are just smoke and mirrors. Still, even the first offers (with “project prices”) often offer negotiation potential in the clear double-digit percentage range – although list prices and already discounts of 30-50% are mentioned in writing on some offers.
Why is this so? A hint can also be found, for example, in the annual report of the system house already mentioned: “This cooperation [between vendor and reseller] involves the yearly determination of individual targets in the business with the respective vendor’s products and services. The vendor incentivises the achievement of the target by granting bonus payments, refunds or marketing grants.”
On the one hand, the system house receives higher discounts than are passed on to the customer, i.e., a margin on the purchase price. In addition, the manufacturers can grant further discounts at will. In addition, large resellers regularly receive rebates and bonuses on the total volume brokered (at the end of the quarter or year).
Thus, even if you demand an open book policy for the project from the system house on the purchasing side, you will never know the total remuneration paid by the manufacturer to the system house. IT security sales are about the same level as financial and insurance sales 20 years ago regarding hidden fees and costs.
It only helps to consistently maintain a competitive situation, ideally paired with independent benchmarking of the offer prices. If this is not possible (e.g., because only one manufacturer can meet the mandatory requirements), an equalisation of a channel partner with the manufacturer should be considered. Manufacturers are reluctant to allow this (for understandable reasons – they don’t want to upset their channels). However, it is possible. The extra effort quickly pays off due to the high cost of many security projects.
Conclusion
While attempts are often made to renegotiate daily rates, the significant savings opportunities in procuring cybersecurity solutions still need to be considered. The interaction between the business department and purchasing, if necessary supported by external specialists, can save time and money while reducing the risk in the selection process. Particularly in times of rising costs across the board, this offers an approach to increase the security level in a targeted manner and to save budgets.
Please remember: This article is based our knowledge at the time it was written – but we learn more every day. Do you think important points are missing or do you see the topic from a different perspective? We would be happy to discuss current developments in greater detail with you and your company’s other experts and welcome your feedback and thoughts.
And one more thing: the fact that an article mentions (or does not mention) a provider does not represent a recommendation from CyberCompare. Recommendations always depend on the customer’s individual situation.







