Hello everyone
Wow, what exciting times – finally something is happening! 😉 You hardly get to write with the flood of messages. Strangely enough, no one is talking about tariffs on Microsoft Windows or M365. It would also be bad for us if the delivery would then be stopped, or the import duties would simply be passed on to the license costs.
The Chinese government has already noticed this problem, apparently a few people have read “The Art of the Deal” in time. There, the use of Windows and Intel has been prohibited by authorities since 2024. Everything runs on Linux derivatives and ARM architecture. So far, the administration in China still seems to be functioning. Perhaps we will develop a real alternative in Europe instead of constantly complaining about the technological leadership of other countries. The development of an operating system ecosystem compatible with Office-compatible office applications should have become much easier with Vibe Coding, and in sales you would get a tailwind from discussions about digital sovereignty. Who knows, maybe the Schwarz Group is already at the start with something like this.
Will we ever see completely independent European offshoots of Crowdstrike, PAN, Cisco, etc. in order to avoid further disadvantages in local tenders (especially in the case of awards by public clients) due to the headquarters in the USA and data protection concerns? That would be possible via spin-offs and licensing agreements with the US counterparts.
According to presumably detailed protection needs analysis, the USA has (almost) cut funding for the CVE program (MITRE ). To be honest, if we all booked a slightly smaller booth at RSA or it-sa, the maintenance of the CVE/CWE/NVD database or the now new ENISA EUVD could easily be handled by a consortium of cybersecurity providers, and the money would be better spent. CISA also seemed to be in little need of protection, where 30-40% of the jobs are now to be cut.
SentinelOne , on the other hand, gets free publicity from the White House – perhaps this will give the European business a similar boost as for VW electric vehicles due to the widespread boycott against Tesla/Musk.
Speaking of MITRE: Depending on the subject area, it is probably worth taking a look at the following publications:
- Emulation plans of the ATT&CK tests: With detailed information to be able to perform the laboratory tests yourself => So you can be inspired by EDR/SIEM for pen tests / red teamings / PoCs
- Examples of detection rules: With systematics and explanations of how the detection of attack techniques such as RPC calls, file downloads, LSASS memory dump, etc. can be improved as specifically as possible, difficult to circumvent and with few false positives
What’s going on at Rapid7? Despite marketing and sales expenditures of 32% (vs. R&D of 16%), sales growth is only 9% to ~750 million EUR. The number of corporate customers is a remarkable 12.000, but is almost stagnating. The share price has collapsed by more than 80% from the all-time high and an activist investor (JANA Partners) has entered. Last year there was a restructuring, obviously successful, because the company is profitable again. But it shows once again: Keeping up with Microsoft, Crowdstrike, Palo Alto, Splunk/Cisco, etc. in the long run is not subject to entertainment tax. Crowdstrike’s advertising budget alone is ~$120 million/year, six times as high as Rapid7’s. And in order to be price-competitive with a Microsoft bundle of Azure, E5 + Defender Suite, EDR competitors now have to “bring money”, to quote a colleague.
The more I learn about data security (DSPM, DLP, DDR) and manufacturers such as Cyera, Rubrik, Varonis, Keepit, etc., the more I ask myself why each company or individual public bodies such as hospitals have to organize and operate this individually. The classification of data according to GDPR, HIPAA or PCI-DSS is valid across the board. The same applies to the necessary retention times. E2E encryption and masking of data between applications can be more easily unified centrally and kept state-of-the-art. And ensuring and testing the effectiveness of the DLP solution used by each individual company seems incredibly time-consuming and error-prone. The same applies to checking whether all data has been deleted in time. Actually, that would be ideal for (European?) Cloud service provider to offer it centrally for customer groups as an add-on of storage and compute, right? Other opinions, of course, are welcome.
After the AI agents and their advantages or pitfalls, the forums and blog posts are now full of reports about MCP (Model Context Protocol). MCP is an open standard and is used by precisely these AI agents to access data and interfaces of tools. The number of MCP servers is therefore increasing rapidly globally. And of course, MCP access can be abused by attackers and must therefore be protected by filtering requests, masking feedback of sensitive data, authorizing configuration changes to the MCP servers, and managing the tokens used by agents to log on to systems, among other things. If you are looking for bad practice examples, you will find them at Damn Vulnerable MCP Server .
Also interesting: Crowdstrike now offers a PAM module, including Secret Vault, dynamic access permissions and session recording. So far, this has been more the domain of CyberArk, OneIdentity, Delinea and BeyondTrust or similar. So here the platform/suite will be further expanded.
M&A Corner:
- KKR wants to take over the German Datagroup , the offer is about 1x turnover and thus about 30% above the market capitalization before offer. Could also become an issue for Cancom or Bechtle (here, however, the founding families still hold large shares) – the stock market prices of the German system houses are comparatively low, while they would certainly be an attractive addition for large Indian players such as Tata or Infosys, for example: synergies on the purchasing side with large vendors and at the same time local presence.
- Allurity (cybersecurity VC fund / platform from Sweden) acquires OneVinn (consulting + MDR on Microsoft Stack)
And of course a few notes from provider discussions:
Appomni:
- US provider of SaaS security, i.e., configuration management (SSPM) and anomaly detection / UEBA / ITDR
- ~230 employees, reference customers including Google, Pfizer, Barclays, Novo Nordisk, Storz, Ifco
- Deployment as SaaS, hosted in Frankfurt for EU customers
- Typical applications for monitoring: M365, Workspace, Hubspot, Salesforce, ServiceNow. For SAP, unfortunately, only SuccessFactors and Ariba are possible so far, no Hana.
- Again, the basic idea: Replace periodic reviews (1x/year or similar) with continuous checking of specifications and accesses. But: Appomni has no write permissions, i.e. only alerting in the event of deviations from policies such as MFA, no automatic change of settings in the sense of system hardening
- Of course, integrated with all common identity and PAM solutions. The enforcement of the policies can then be triggered via Entra, CyberArk, etc
- Normalization and pre-filtering of SaaS logs for SIEM
A-Lign:
- American provider of security and compliance audits: More than 400 auditors, > 5000 SOC2 audits carried out, in the EU primarily ISO and C5 audits, i.e. competition with TÜV, DEKRA, PwC, EY, KPMG, etc.
- Several thousand customers, including American Express, Procter+Gamble, AON, WTW, Siemens Medical, Eviden, ING, London Stock Exchange
- Auditors for EMEA clients are primarily based in Bulgaria
- According to its own statement, it is significantly cheaper than the Big 4, but already with similar credibility in the USA. Brand awareness in Europe can of course still be expanded.
Trio:
- Manufacturer of OT/IIoT solutions and software development from Lübeck (nice!)
- Has been around for ~25 years, ~80 employees, now belong to Viega. Approx. 30 corporate customers, including VW and Dräger
- Patented solution covers functions of segmentation firewalls, bidirectional protocol converter (e.g. between Modbus or SMBv1 on the OT side and OPC-UA or SMBv3 on the IT side) and secure remote access
- Deployment: Containers on servers, no agents on OT target systems
- Also offered as a managed service
- Certified according to IEC 62443 4-1, in addition to TISAX and ISO27001
Hackrate:
- Bug Bounty Management, Vulnerability Disclosure Management and Pen Test Provider from Hungary
- Approximately 3400 pen testers/researchers using the platform; approx. 25 corporate customers
- Special feature: For this purpose, there is a Layer 7 Gateway (“Hackgate”) as an on prem appliance or SaaS, which has the following main functions:
- Recording of the tests
- Structured quality check allowed when testing web applications, e.g. which OWASP risks were tested for which assets in the scope
- Comparison of the test duration with the booked time quota
- Feedback to pen testers on efficiency and effectiveness compared to the benchmark
- And of course, the access of the testers can be technically restricted via the gateway
- At the introduction, I had the impression that life as a pen tester is getting more and more difficult – the bar is being raised every day. Fortunately, there are of course more and more open source tools for support, such as “Document my Pentest“, to automatically create reports based on the observed test steps.
Elisity:
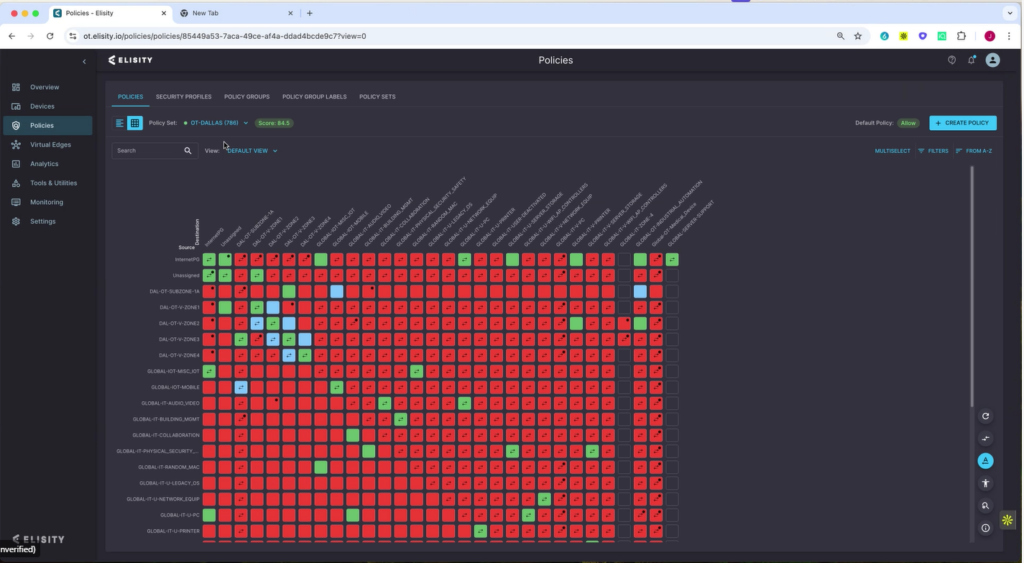
- US provider of network (micro)segmentation (IT, OT / IoMT), reminded me of Zero Networks, Color Tokens or the microsegmentation of Akamai
- Approx. 100 customers, including GSK and some other pharmaceutical companies
- Flexible yet comprehensive deployment: Local VM connected to switches/routers/FW/OT NIDS or similar, SaaS and local agents on switches
- Policies can be proposed on the basis of the previously detected network traffic in a training phase, or on the basis of logical characteristics (similar devices, locations, etc.) and then adapted by the customer
- Integration with Identity Provider = > Policies + Conditional Access at the user level possible
- If the customer uses application layer firewalls, the rules can also be adjusted accordingly granularly
- Chic overview of the network segments with actually possible connections (see screenshot)
As always: Questions, suggestions, comments, experience reports and also opposing opinions or corrections are welcome by email. Ditto for unsubscribing from the mailing list.
For the people who have received the market commentary for the first time: Here you can register if you are interested or work through the archive.
Regards
Jannis Stemmann






