Hello everyone
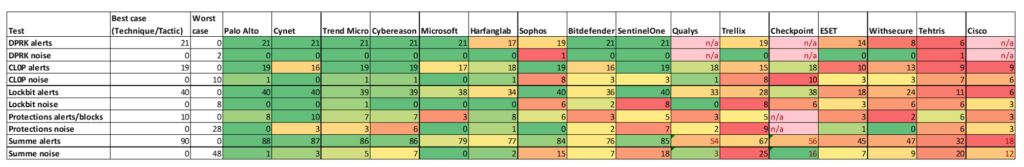
I hope everyone had a good start into the new year! Shortly before Christmas, MITRE published the latest results of the Enterprise EDR evaluation (DPRK, Cl0P, Lockbit). Here are my key takeaways from it:
- As a novelty, benign background traffic (“noise”) was emulated and as a result, of course, there were false positive alarms of the EDR tools, which were also evaluated
- The test environment also included a macOS system for the first time to specifically map the attacks from North Korea. Overall, however, the test environments used are still very small compared to a real infrastructure (3-4 servers, 3-4 clients). It is therefore all the more surprising that clear differences in detection and protection rates come to light.
- Cynet finally took part in the test again and did very well again (Cynet has often offered very cheaply in the past, either with its own MDR service or in German from Deutsche Telekom, among others)
- Otherwise , Palo Alto, Trend Micro, Microsoft and Cybereason are among the top 5 this time according to my interpretation
- Cisco (Secure Endpoint) seems to have been totally the worm in it
- Trend Micro and Sophos generated about 100-1000 times as many alarms as the other established solutions, but still with comparable selectivity (ratio of true to false positives). The alarm volume is driven by the “medium” Severity. I would say that in practice this is almost irrelevant for SOC analysts, because the medium severity level is only used for enrichment / proactive threat hunting. If I’m wrong, please let me know.
- Qualys (Multi Vector EDR) had an even higher alarm volume – seems to take some time before it becomes a full-fledged EDR. But the goal seems to be clear.
- Qualys, Checkpoint (Harmony Endpoint), and Cisco did not pass the DPRK test. At least Cisco advertises MacOS compatibility. Humph.
- Strangely enough, Crowdstrike was not there – they probably dropped out before the test began, even though they were originally registered. Broadcom was also not represented with a solution.
- Overall, MITRE has never created a ranking (this also allows each manufacturer to evaluate individually and to choose itself as a 100% winner). In my opinion, however, it is unnecessarily difficult to evaluate the test results now published, in view of the fact that the individual tests cannot be aggregated by manufacturer and no summary of the results by manufacturer can be displayed in the protections. However, the MITRE team around Greg Fischer is ready to answer any questions.
Below is a table with a first evaluation, in which we only counted those with assignment to a technique/tactic as successful detection (I think this is in the spirit of the inventor). If anyone does not agree with our methodology, or if we have made mistakes in the rather manual transfer, please feel free to contact us. And please understand the ranking only as an indication.
The DCSO Incident Response Team has posted an interesting blog detailing the recovery of partially encrypted files after an Akira ransomware attack (NTFS partitions of VMWare ESXi Virtual Disks). Why were only small fragments of the files encrypted? To delay the time until discovery on the attacker’s side (e.g. via CPU load and file integrity) and to at least damage as many files as possible during this period.
For hardening ESXi systems, there is this easy-to-read article with recommended measures (such as disabling SSH, MOB, CIM and other services, account lockout settings, UEFI Secure Boot) from Sophos, slightly shorter than the CIS benchmarks. With hypervisors, the problem is usually that no EDR agents can be used directly on them, but e.g. the detour via logs/SIEM has to be taken.
For company acquisitions (M&A), approximately USD 45 billion was invested in ~270 significant deals in the cybersecurity sector in 2024 (source: Return on Security). This is about 10% more acquisitions and deal volume than in 2023. The last headlines that caught my eye:
- Arctic Wolf is taking over the Blackberry EDR Cylance (I guess, mainly because of the customers – didn’t have the impression that Blackberry has invested much in the last 2-3 years. On the other hand, Arctic Wolf will then be able to offer more from a single source, especially for smaller medium-sized companies that did not previously have an EDR)
- Fortinet has acquired Perception Point , strengthening its position in the field of email security and enterprise browsers. I have to take a closer look at the latter, looks similar to LayerX at first glance.
- The German Zero Trust provider DeviceTRUST has been acquired by Citrix
- 1Password has acquired Trelica (a provider for the discovery of used SaaS apps)
Here are a few highly speculative hypotheses (“predictions”) for 2025, let’s see what will come of them:
- The number of cybersecurity IPOs will at least triple compared to 2024 (i.e., from 1 to 3). Wiz , for example, is already in the starting blocks
- Google buys an EDR provider
- Cisco/Splunk buys either a “real” EDR vendor or a cloud/data security vendor
- Microsoft is really turning up the heat with Defender for IoT (formerly CyberX) in the NDR + OT NIDS market in terms of advertising+sales/bundle pricing, after the last few years (in my perception) it was more about integration with Defender and Sentinel as well as further development for Enterprise IoT. If applicable, the competitors can dress warmly.
I am happy to receive other theses on the course of the year – no one will be wrong more often than me, so no false restraint 😉.
And if you are interested, here is the notepad from some provider talks:
Gatewatcher:
- French provider for NDR, i.e. market support for Vectra, Extrahop, Darktrace, Exeon…
- Approx. 150 employees, ~50 corporate customers (including French banks such as BNP, Crédit Agricole)
- Architecture completely on premise, i.e. not only the taps, but also the central engine
- Incl. Deep Packet Inspection, e.g. for the detection of LDAP scans, but essentially based on the Suricata IDS
- Cloud endpoints can be connected via sensors
- Timing for updates of signatures and algorithms can be set by the customer
- Pattern recognition for encrypted traffic
- Eigener CTI-Feed (ähnlich Recorded Future etc.)
- Also relatively many SIEM/SOAR-like functions (threat hunting in old data, enrichment with EDR telemetry via queries, playbook creation for isolation of endpoints). Ring buffer up to 1 year possible, storage period for data types can be individually set
- Licensing based on number of IP addresses and coverage modules, even offer purchase of the software as an alternative to subscription
- Still looking for MSSP partner for the DACH region => Maybe interesting for some readers
Commvault (Update):
- Most people probably know this as a backup/recovery alternative to Rubrik, Cohesity, VEEAM, IBM or Acronis
- ~2800 employees, approx. 100k organizations as customers, public references including NTT Data, Sony, Dow Jones, Coca-Cola and in our climes Olymp and Adidas
- Backup of cloud workloads not only via agent installation, but also as a SaaS service in a separate customer tenant
- Self-service by users for recovery of individual files, but depending on the storage provider, indexing is necessary for the search of blocks
- Deception software that runs on a VM in the network and emulates device dummies (e.g. switches, servers, PLCs)
- Many DLP functions, including data classification: Automated recommendation for classification, can then of course be adjusted manually
- Entropy detection of source data during backup process to prevent overstorage of good data with infected data as much as possible
- Offer table top exercises (free of charge, depending on the customer situation)
Contrast Security:
- US provider for Application Detection & Response (similar to Miggo), plus SAST, DAST, SCA and Runtime Tests
- I.e., AppSec along the entire value chain of own code, 3rd party libraries and protection during execution
- 330 employees, 250 corporate customers, including SAP and BMW, German-speaking team on site
- Vulnerabilities in supply chain: Filter by actively used classes or libraries at runtime possible => Effective prioritization with low false positives
- Runtime monitoring and, if necessary, termination of execution by sensors (= code snippets): http, data flows, code, libraries, config. Most popular languages and frameworks such as Java, .NET, PHP, JS, Golang, Python etc. are supported. Processor load probably typically increases by 10-15%. Of course, a good interim solution until patching. To do this, the WAF can be optimized to block less benign access.
- With DAST, you can jump exactly into the problematic lines of code
- Excellent performance compared to all competitors in the OWASP benchmark
- Licensing: IAST (Interactive App Sec Testing) via number of applications (microservices are combined), Runtime Protection depending on the number of running instances
- Naturally integrated into the SecDevOps toolchain such as Jenkins, Slack, Git* and secure coding platforms such as Secure Code Warrior
- Easy tracking of MTTR
Fastly:
- US provider of CDN, WAF, DDoS / botnet protection and API security, including customers such as Spotify and Disney+
- As the name implies, Fastly wants to score points with speed / performance compared to other providers:
- According to publicly available tests such as CDNPerf or a data evaluation of the Google Chrome UX Report , Fastly is actually one of the faster CDNs. The availability according to Real User Uptime seems to be inconspicuous (slightly worse than e.g. AWS Cloudfront or Cloudflare, but slightly better than Akamai or Google Cloud CDN)
- Implementation of configuration changes < 30 ms
- Purge Time < 150 ms (apparently important for highly up-to-date information such as stock market prices or sports betting results)
- Decision Time WAF (Block/Pass Traffic) von unter 1 ms
- WAF can also be installed on prem or in containers with identical functionality
- Allegedly, the WAF is immediately used by most customers without tuning in block mode, as proprietary detection algorithms are used in addition to the OWASP Core Rule Set (CRS) signatures. However, other providers also claim this, e.g. open-appsec or Checkpoint, which have published a well-explained WAF benchmarking on false positives/false negatives (and of course also came out on top in their test)
- Unfortunately not yet in the BSI’s list of qualified DDoS mitigation service providers (but it won’t be long, I think)
As always, also in the hopefully healthy and successful new year: Questions, suggestions, comments, experience reports and also opposing opinions or corrections are welcome by email. Ditto for unsubscribing from the mailing list.
For the people who have received the email: Here you can register if you are interested.
Regards
Jannis Stemmann







